Introducing RunReveal Enrichments because every log needs a little more context

Today we're announcing custom enrichments and providing the functionality to RunReveal customers. Enriching your logs with additional information is one of the simplest and most effective methods to make each log more meaningful. RunReveal is now providing this functionality through a full featured API to our customers.
Your security logs are generated by hundreds of disparate systems where each individual system knows nothing about the others. Looking at any individual log only offers a view into that single event and this obvious but frustrating fact is what makes detection really really hard.
The result is every security team has mountains of logs laying around that they don't know what to do with and struggle to understand. Enrichment can help to solve this problem by adding information that gives each log a deeper and more obvious meaning, allowing for better alerts and avoiding manual work during an investigation.
How do enrichments work?
The most common example of an enrichment is attaching IP information or reputation to a log. At RunReveal we already did this by attaching several fields to all of our logs that we thought our customers would want.
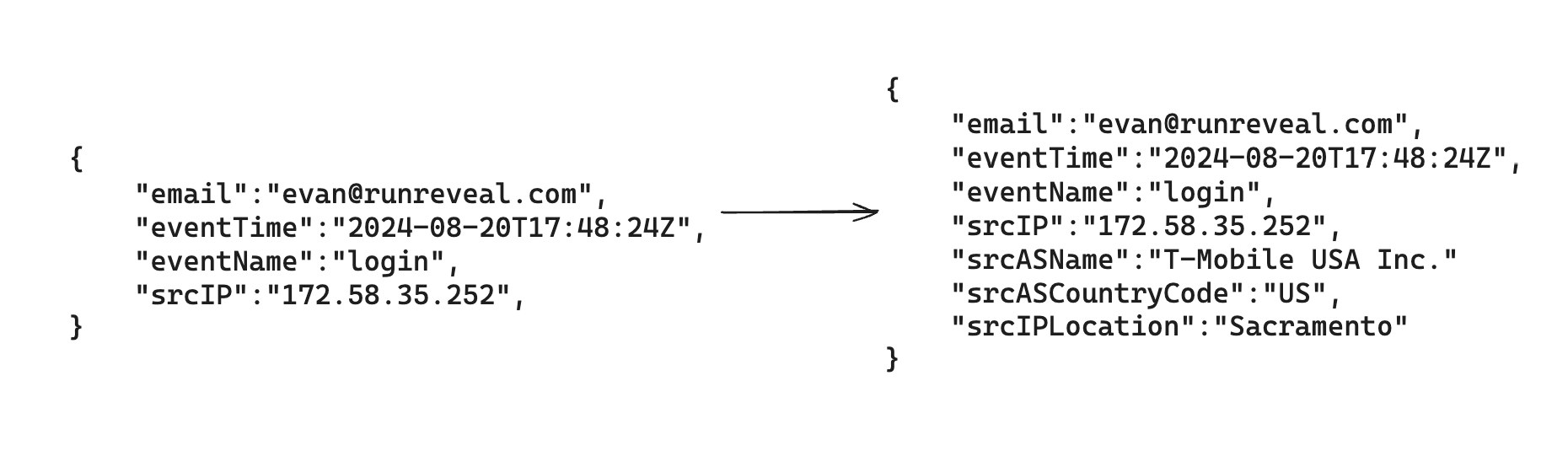
In this classic enrichment example the general steps needed to perform this kind of operation are:
- Lookup of a field used for the enrichment (in this case
srcIP) - Search for the additional data that should be attached to the log (
srcASName,srcASCountryCode, andsrcIPLocation). - Rewrite the log to contain the additional fields.
We built our enrichment product to function exactly like this. Enrichments first specify a field used to perform a lookup. Next, customers match against that field using regex, IP CIDR comparisons, or directly with string comparison. Lastly a set of KV pairs are then attached to the log in the OCSF Enrichment format.
Configuring an enrichment in RunReveal using the UI is simple. Here's an example of adding a human readable label to our Cloudtrail logs that indicate it's our production AWS account.
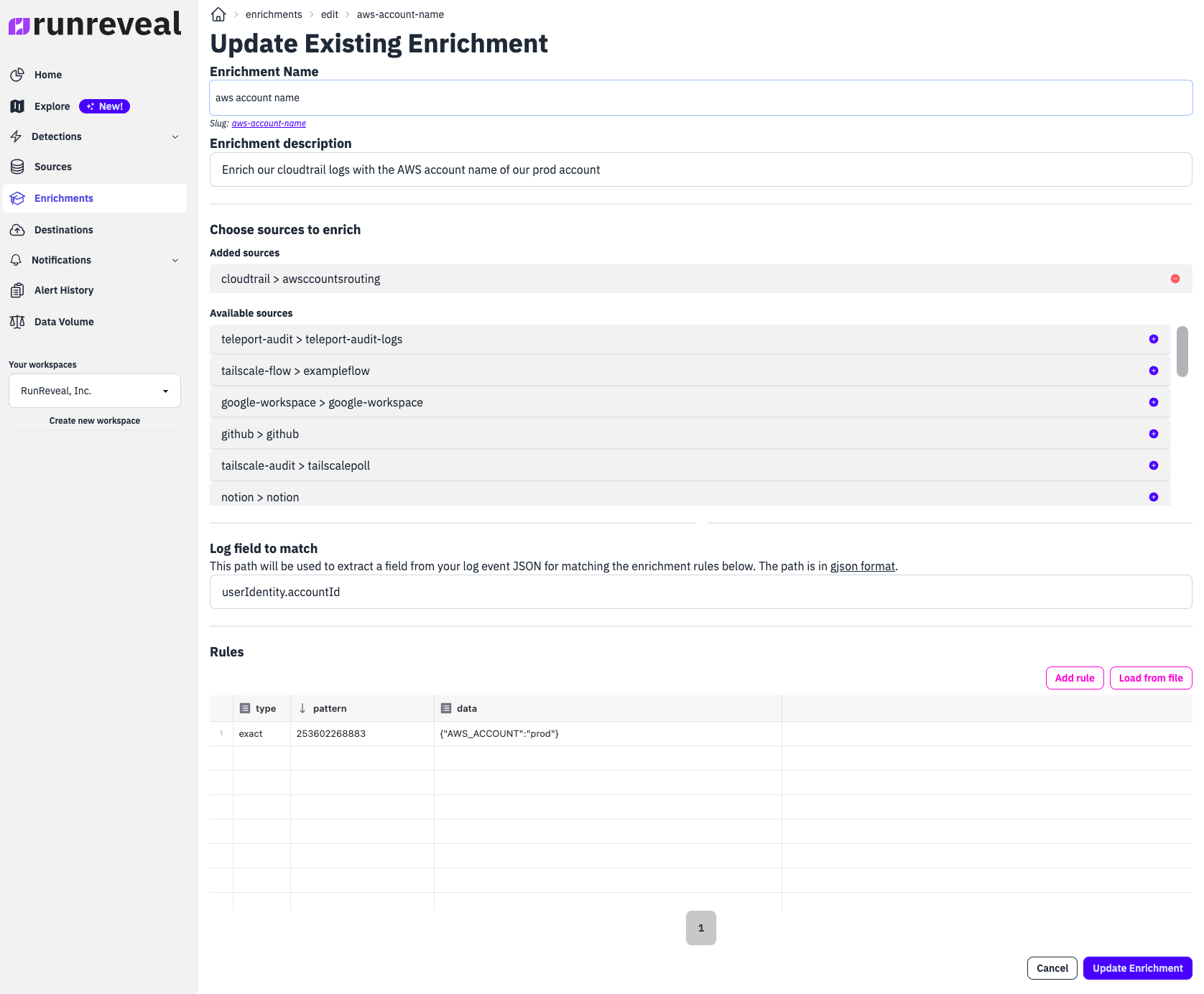
The reality is many enrichments will have many rules with potentially thousands of patterns, so we support uploading files or using our API to upload large numbers of enrichment rules too.
How to waste time and money on your SIEM
There's no single way to contextualize your logs but it's a good rule of thumb that doing it earlier in your security logging pipeline is better. By performing this step as early as possible you avoid potentially costly problems.
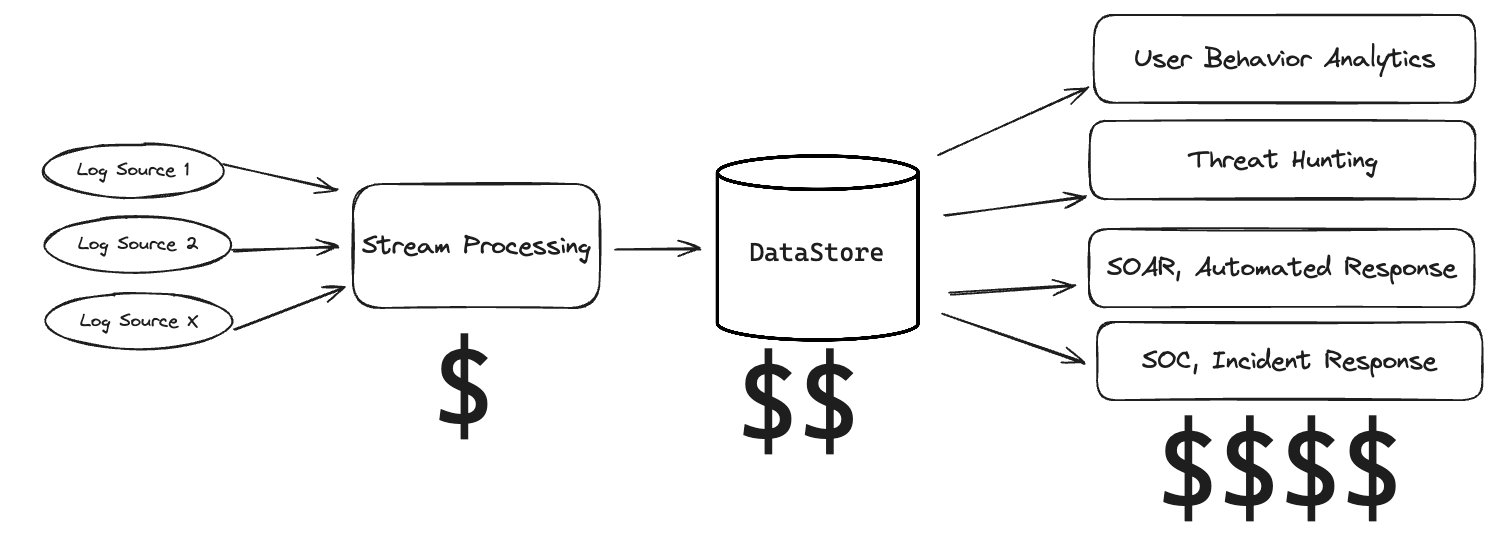
The two biggest ways that costs start to add up is through data decay and increased load on your SIEM.
This talk by Josh Liburdi at BSidesSF a few months ago shows a bunch of interesting examples of data decay and makes it very clear why enriching a log early is the best option. For example, the location data associated with an IP address changing could cause the answer to "Where was employee X on August 22, 2024?" to be completely different from one day to the next.
Additionally, enriching logs after they've been written to your SIEM increases costs and datastore load. It requires running more queries to get the same information that could have been attached to the log via an enrichment. By enriching logs earlier in the pipeline you incur a one-time cost and reduce overall query load on your SIEM.
There's no silver bullet when it comes to security logging but "shifting left" when it comes to detection engineering is an incredibly important concept to avoid wasted time and money.
What's next
Enrichments are an important building block to help our customers contextualize their logs. We plan to mature this product over time with more features and some automated enrichments for common use cases.
RunReveal started by collecting logs into a database and making those logs useful for detections, threat-hunting, search, and building dashboards with very little effort. We've learned there are a ton of other use-cases too. The architecture that security teams need to help manage their data needs to be flexible which is why we added destinations, bring your own database, enrichments, and more coming soon.
If you want to learn more about RunReveal you can try it now yourself or book a demo with our founders and see a sneak preview of what's coming next.

