The RunReveal Remote MCP Server
Launch of RunReveal's Remote MCP Server enables AI-powered log investigations with OAuth. Transform security ops in minutes, not hours.

We're thrilled to announce the launch of our Remote Model Context Protocol (MCP) Server, a powerful new tool that enables anyone to conduct thorough investigations over every kind of log.
A few months ago, we released a local MCP server using our RunReveal CLI. Our customers are using it daily for investigations and say it would be painful to return to doing investigations without it, so today we're making it exponentially easier to set up. The Remote MCP Server is available early access to all our customers today.
The easy button for MCP-powered investigations
With the local MCP server, installing a binary and configuring it for various clients using API keys when the different clients have different ways of injecting environment settings (or not at all) is cumbersome and error prone. Conversely, setting up the remote MCP server couldn't be more simple 💥.
Now, all you need to do is add the RunReveal MCP URL into your client, authenticate the session using OAuth (selecting the proper scopes for the tools you want to use) and that's it—you now have very impressive, superhero-like capabilities to query logs at the speed of MCP.
Our platform has been optimally built to aid these investigations to provide needed context instantly using model context protocol. We've seen the MCP server used to conduct all kinds of real-world investigations:
- Auditing 3rd party SaaS vendors and developing minimal access policies.
- Getting the current configuration of our AWS infrastructure to help plan infrastructure changes.
- And notably — identifying threats from activity based on historical behavior.
Demo
Investigating your logs has never been easier, so let's see how easy it is to set up with Anthropic's Claude.
- As a Claude administrator, navigate to: https://claude.ai/settings/integrations
- Put these values into the form.
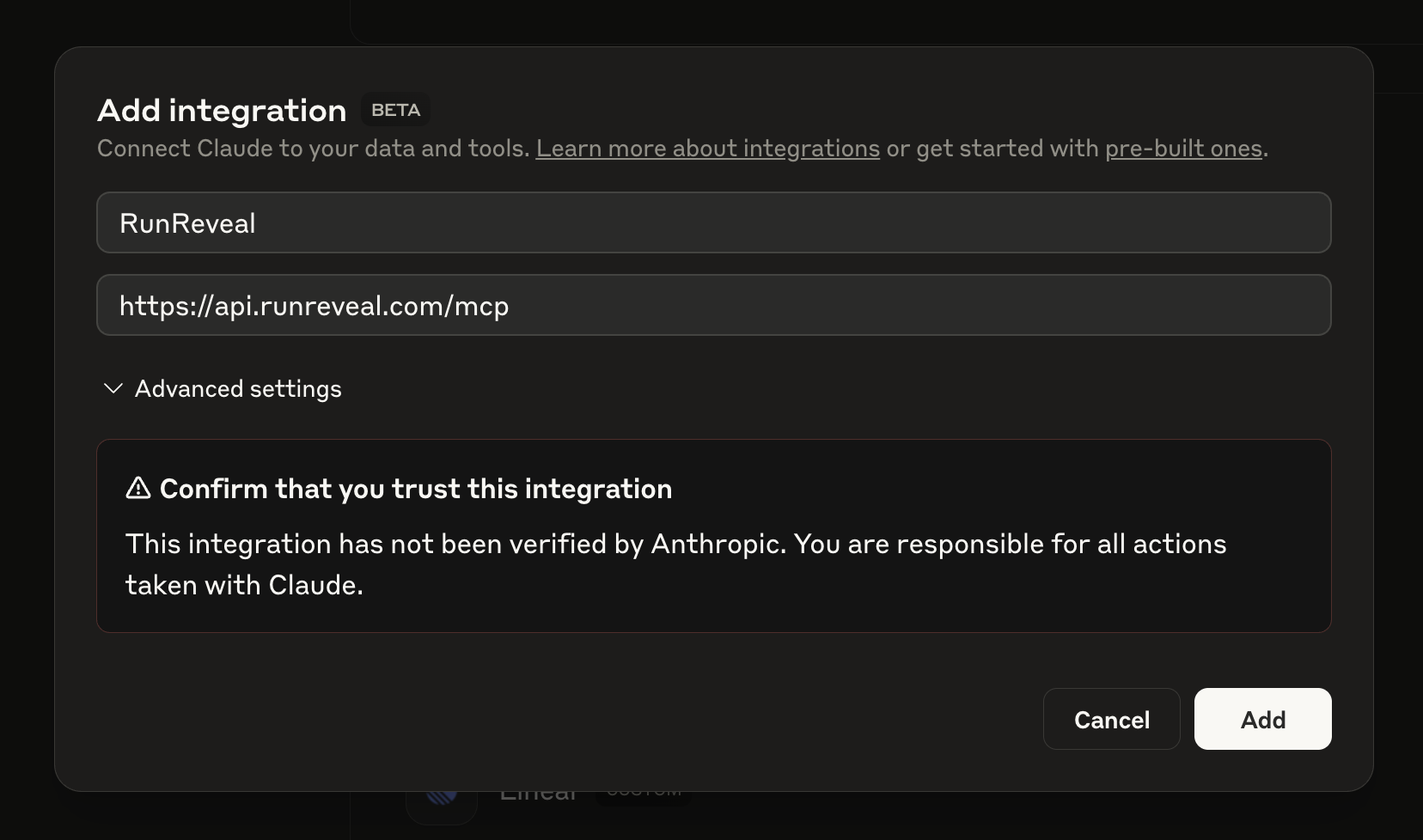
- Hit "Add". That's it! You're done.
On your next chat, you'll have to authenticate via OAuth, selecting Queries & Detections, Read & Write scopes, and then you'll be kicked back to Claude to start your first investigation. 🎉
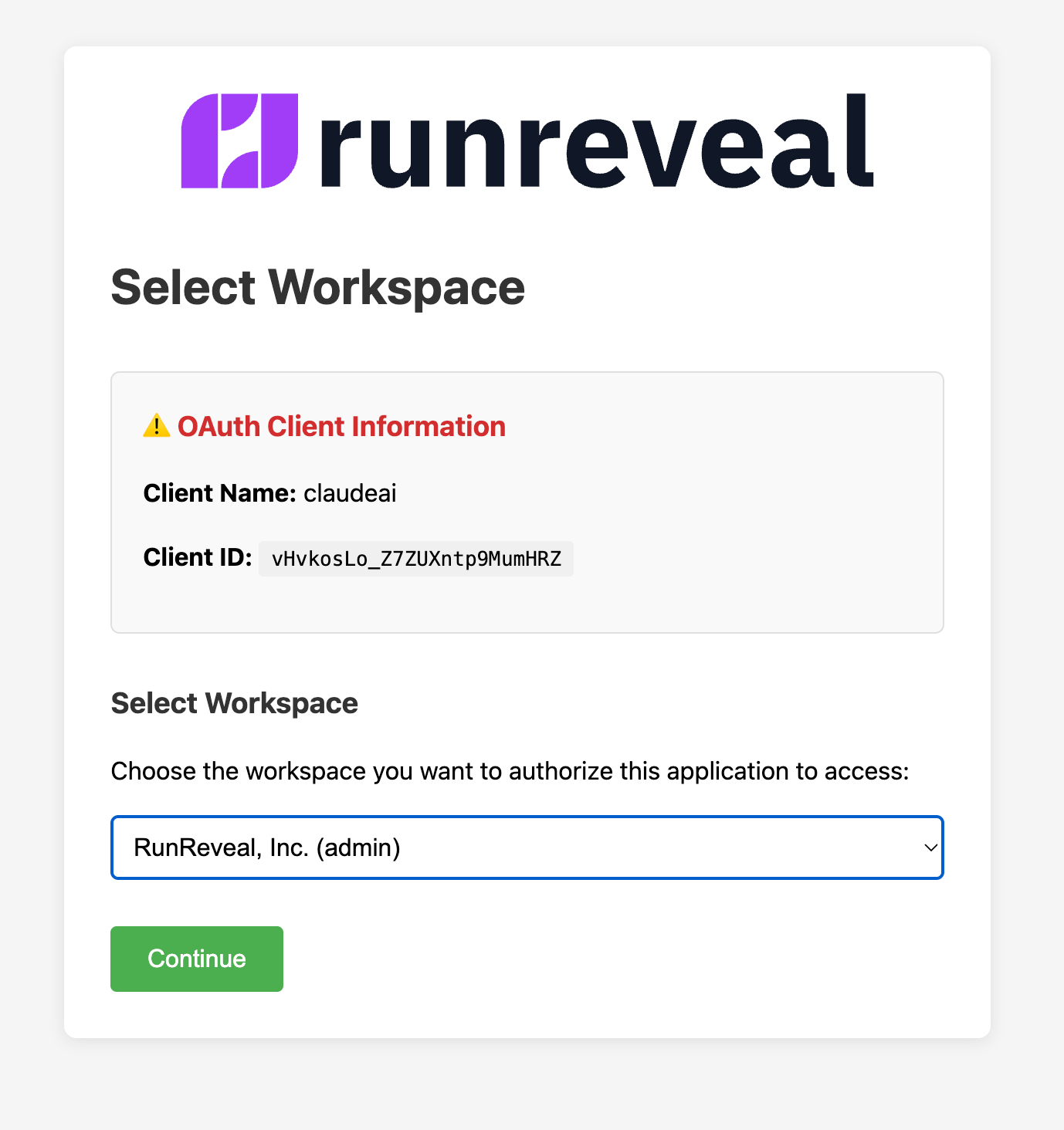
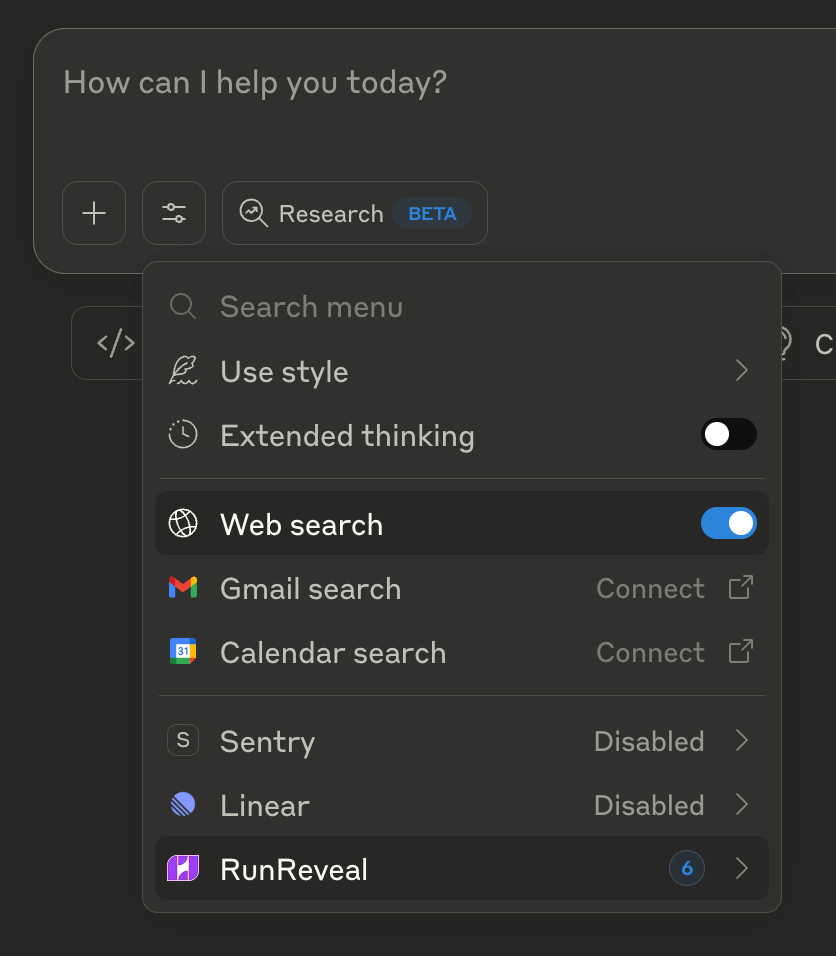
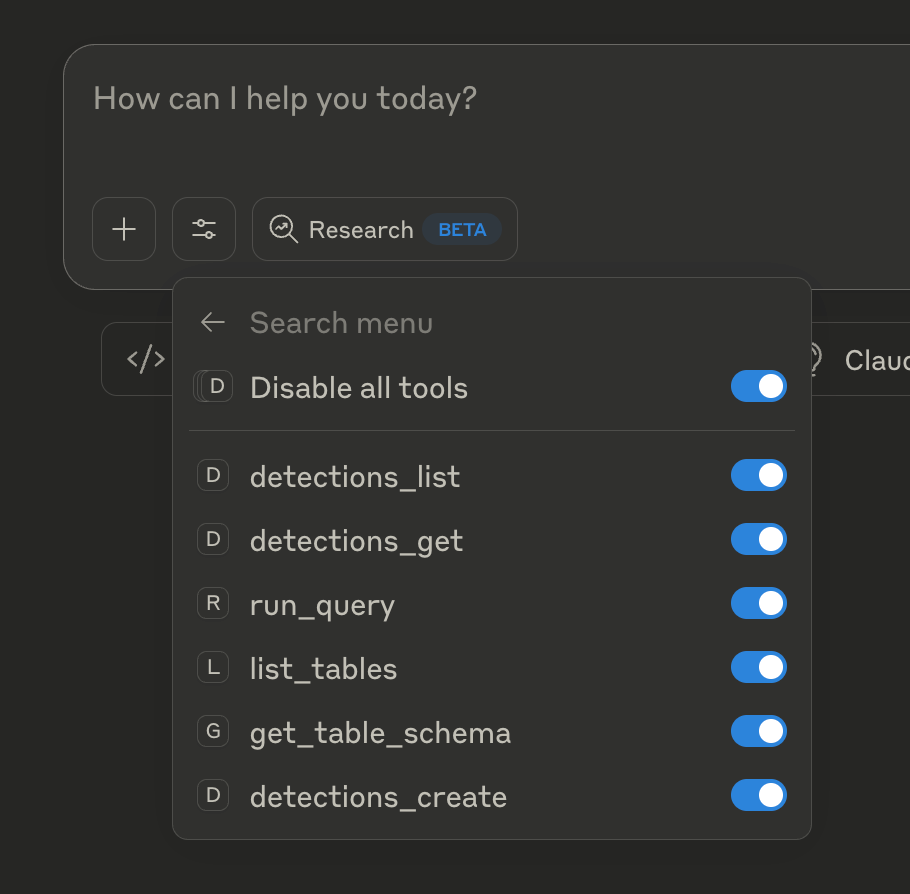
Setup flow for Remote MCP
The technical challenge: Why building a remote MCP server is difficult (but worth it)
Creating a production-ready remote MCP server involves solving several technical challenges, most notably OAuth authentication and scope management and keeping tool calls in sync. Here's how we tackled them.
OAuth implementation with granular permissions
One of our biggest challenges was implementing OAuth in a way that was sustainable and compatible with our existing RBAC framework.
To accomplish this, we made it possible to map OAuth scopes directly to our permissions, bypassing roles for OAuth sessions entirely and allowing for fine grained permissions management when granting OAuth scopes.
Currently, the only OAuth scopes required are Queries & Detections — Read and Write for all the tool calls available in our Remote MCP server today, but as we add more tools, more permissions will be necessary to grant. Speaking of more tools –
Auto-generated tool calls: Keeping pace with change
To keep up with the rapid pace of development at RunReveal, we've invested in creating a library which helps us in auto-generating code that calls our APIs, including MCP tools. What this looks like is implementing RPC-like functions which serve as the HTTP handlers themselves, with serialization and errors handled transparently by the library.
func (s *Server) ListTables(ctx context.Context, in types.ListTablesRequest) (*types.ListTablesResponse, error) {
wksp := WorkspaceFromContext(ctx)
tables, err := s.evtdb.GetTables(ctx, wksp.ID)
if err != nil {
return nil, err
}
resp := &types.ListTablesResponse{
Tables: make([]string, 0, len(tables)),
}
for _, table := range tables {
resp.Tables = append(resp.Tables, table)
}
return resp, nil
}
// elsewhere in the package, we register this with our HTTP Router:
r.Handle(types.RouteLogsQueryListTables,
s.AuthWksp(rpc.RPC(s.ListTables, rpc.WithTag("mcp", "true")), PermQueriesRead),
).Methods("POST", "OPTIONS").Name("list_tables")Once this is registered with a route in our server, we can then use go generate to generate the following code for our MCP tool registry, which is used to determine which API endpoint to call:
"list_tables": {
method: "POST",
path: "/logs/query/list-tables",
description: "RPC endpoint: /logs/query/list-tables (POST)",
inputSchema: json.RawMessage(
`{"type":"object","properties":{},"additionalProperties":true,"$schema":"http://json-schema.org/draft-07/schema#"}`,
),
}This example is fairly trivial (to keep code concise for this blog post), but the more complex endpoints have the full JSON Schema needed by MCP to translate request and response types.
What's next: The future of AI-powered security operations
With Remote MCP, we're just getting started. Our roadmap includes exciting features that will further transform how security teams work. We will continue to expand the tools available to agents, and we will also start reintegrating some of these investigation insights back into the product. Stay tuned for exciting announcements related to that in the coming weeks.
Join us in shaping the future of security operations
Our Remote MCP Server represents a fundamental shift in how security teams can leverage AI. By providing secure, controlled, and auditable access to AI capabilities, we're enabling security teams to:
- Investigate alerts and incidents in minutes not hours
- Uncover hidden connections across disparate data sources
- Maintain complete control and compliance
- Meet the demands of incident response with your existing team
- Become Superhero-like even…
Ready to transform your security operations? Get started today or schedule a demo with our team.
We can't wait to see what you'll build with our Remote MCP Server. The future of security operations is here, and it's powered by AI—safely, securely, and under your complete control.

