Why RunReveal helps companies detect threats with their Okta logs for free

If you're an Okta customer then it's safe to assume that Okta is a critical application of yours. For a lot of companies it is the single portal that their employees use to access all work applications, and it enforces some of the most foundational security controls.
Your Okta logs are so important that RunReveal helps you collect, clean, detect, and search these logs for free. The reason we do this for free is because they are really tiny and provide a ton of security benefit without costing us more than a few pennies.
Last week RunReveal was a finalist at the Okta startup competition at Oktane in Las Vegas. Make sure to check out our video from the competition, and we're super thankful for having had the opportunity to showcase our product.
The Basics of Security in one place
Out of the box, Okta logs provide a really good picture of your total security posture. Without much work you can quickly deduce where your employees are accessing applications from around the world, what kind of security controls are being enforced, and which applications employees use on a day to day basis.
Here's an example of what it looks like to investigate where failed login attempts are coming from. If you're collecting, indexing, and making your logs searchable by each column there's no limit to what you can figure out from your Okta logs.
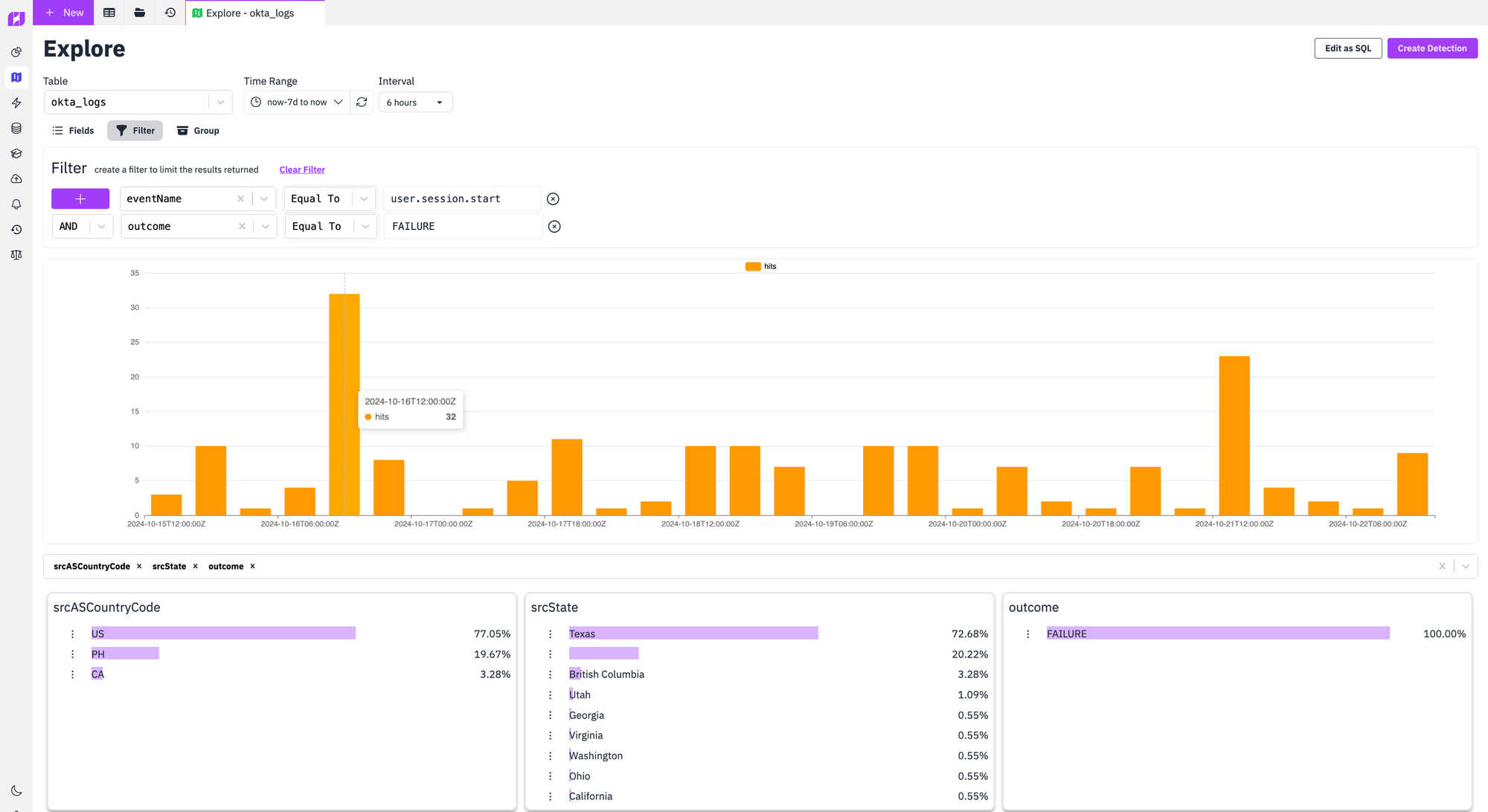
In fact, Okta includes their own threat intelligence in their logs that makes it easy to do some basic identification of threats; including new devices, new geographies, new networks, and other signals that are relevant from a security perspective. Here's what it looks like to use RunReveal to search for logs containing threat signals provided by Okta.
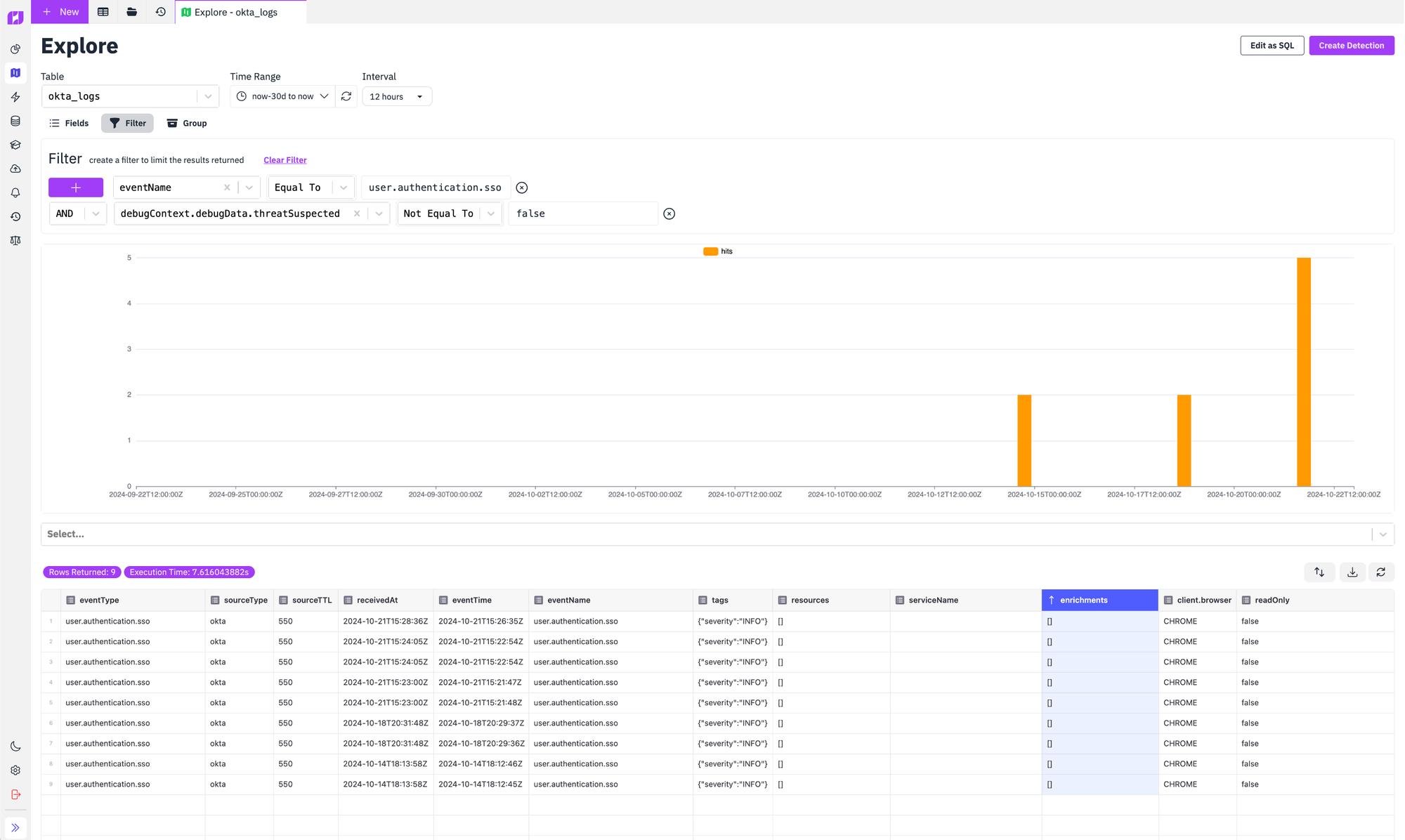
Building out your suite of detections
RunReveal has a bunch of out-of-the-box detections to help our customers get a baseline of coverage for their Okta account. RunReveal provides these to help you gather insights from your logs when you set up an Okta source in RunReveal, and they are all fully customizable.
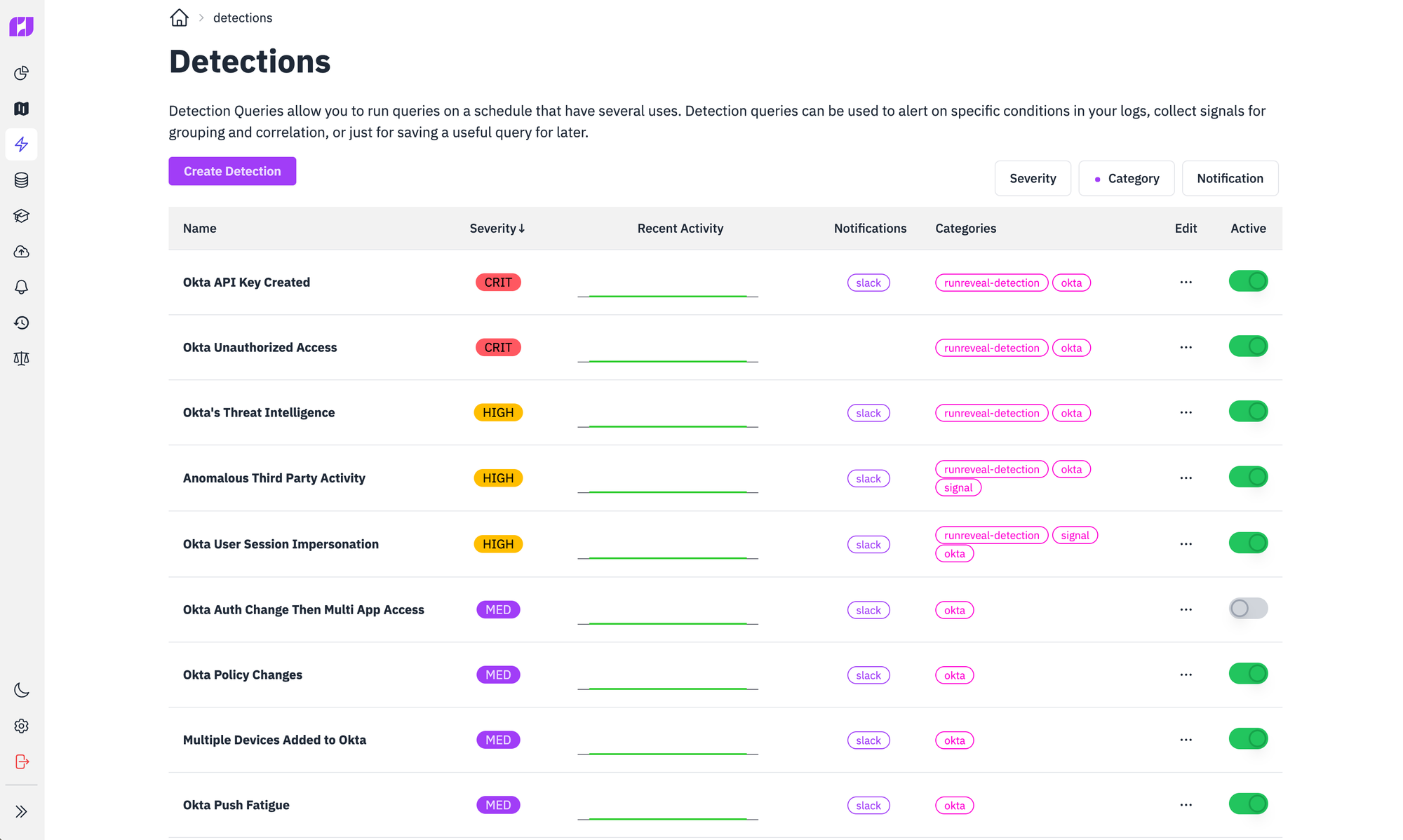
Okta can easily detect things like when a user signs in from a new network, a new country, or a new user-agent. These signals by themselves aren't worth alerting on because they are very common and would cause a ton of false positives. RunReveal helps you surface signals that aren't alert-worthy as interesting by sending you a daily email report about them.
Once you get a handle on your Okta logs and start collecting other logs that matter to you then you can write detections that automatically makes use of our correlation engine. We look for situations where some kind of suspicious access is gained in your Okta account and then suspicious activity in other applications is seen.
By correlating multiple signals into alerts, not just a single "suspicious login" or "new location" event, we can drastically cut down on false positive alerts.
If you're interested, you should check out the technical details of how we implemented correlated alerting here:
https://blog.runreveal.com/introducing-correlated-alerting-a-new-method-of-detection-that-optimizes-for-high-signal-alerts/
Keep your raw logs for the long term with destinations
Okta activity logs expire after just 30 days of being available in their API. One trend we're seeing is keeping the raw data around for much longer than the typical 1-year of retention. We're seeing this trend because storage costs have gone down relative to compute, and because those logs could potentially be very useful if you're dealing with an incident or have some future custom use case.
Some other use cases we've seen folks doing is loading their data into a home-brew SIEM like BigQuery or Snowflake for investigations or forensics, and building custom ML models with a few years worth of your Okta logs. The options start to appear once you have the raw, normalized, and cleaned data in one centralized place like Amazon S3.
RunReveal helps you do this by collecting, normalizing, enriching, and then routing your data to your own blob storage destinations. Setting it up just requires providing us with a bucket and a role, and we'll do the rest by batching your logs and writing them at a regular interval.
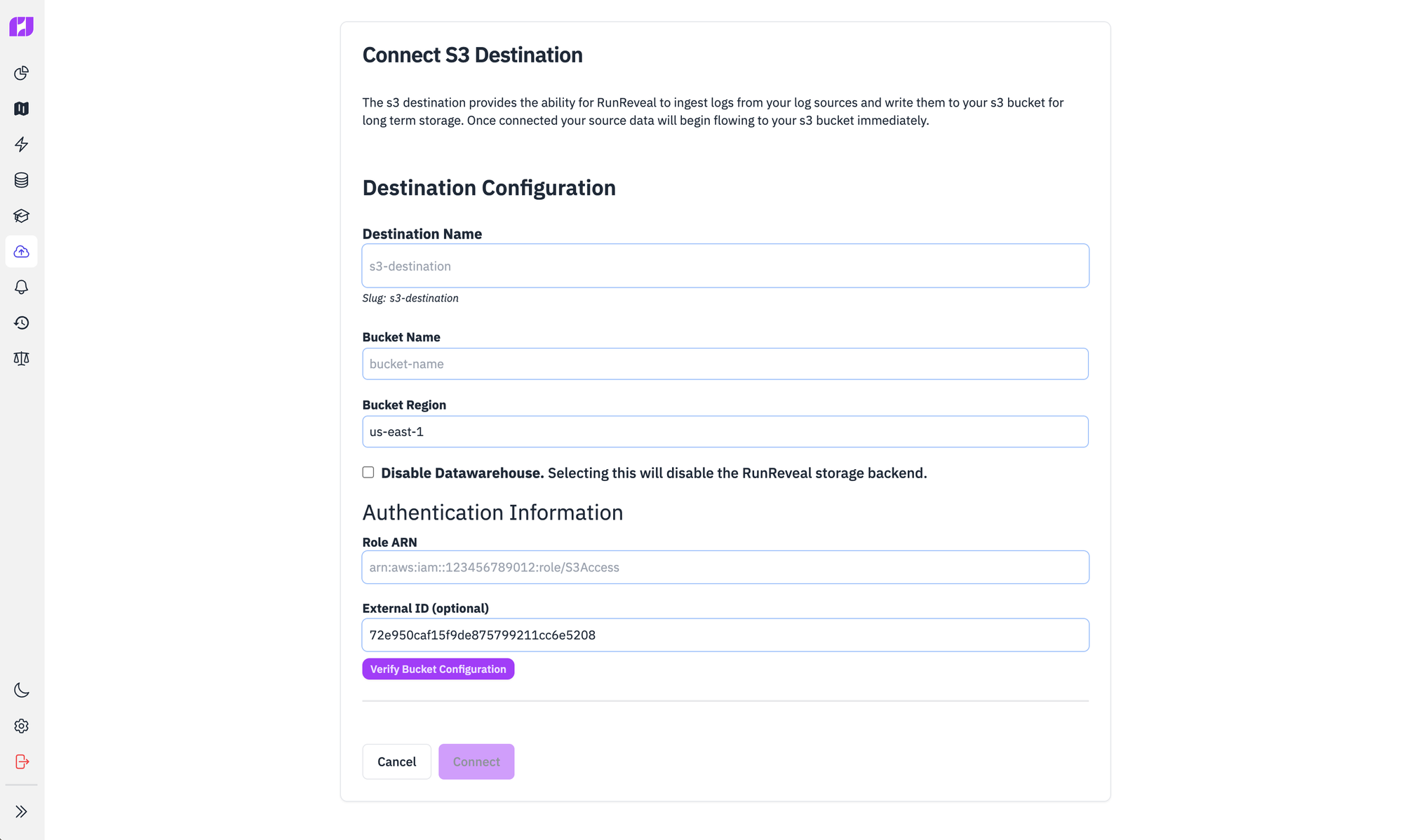
How are you using your Okta logs?
Whether you want to debug someone's access problems or build your own ML model for detecting anomalous access to your production systems, RunReveal built support for Okta logs to be free because it's such a critical application.
Collecting your Okta logs only takes a few minutes to set up and configure. We only require a read-only API key and your Okta subdomain, then we'll backfill your previous 30 days of Okta logs in just a few minutes so you can start to analyze access patterns and begin to understand the exact requirements of your business.
You can try this out now, but if you're curious to learn more before trying it then feel free to contact us to get a demo.

