Visibility in every domain with RunReveal’s AI features
Discover how RunReveal's AI agent transform security investigations from hours-long manual processes into 90-second automated reports. See real examples of AWS third-party risk analysis, network monitoring, and corporate data audits that previously took entire days to complete.

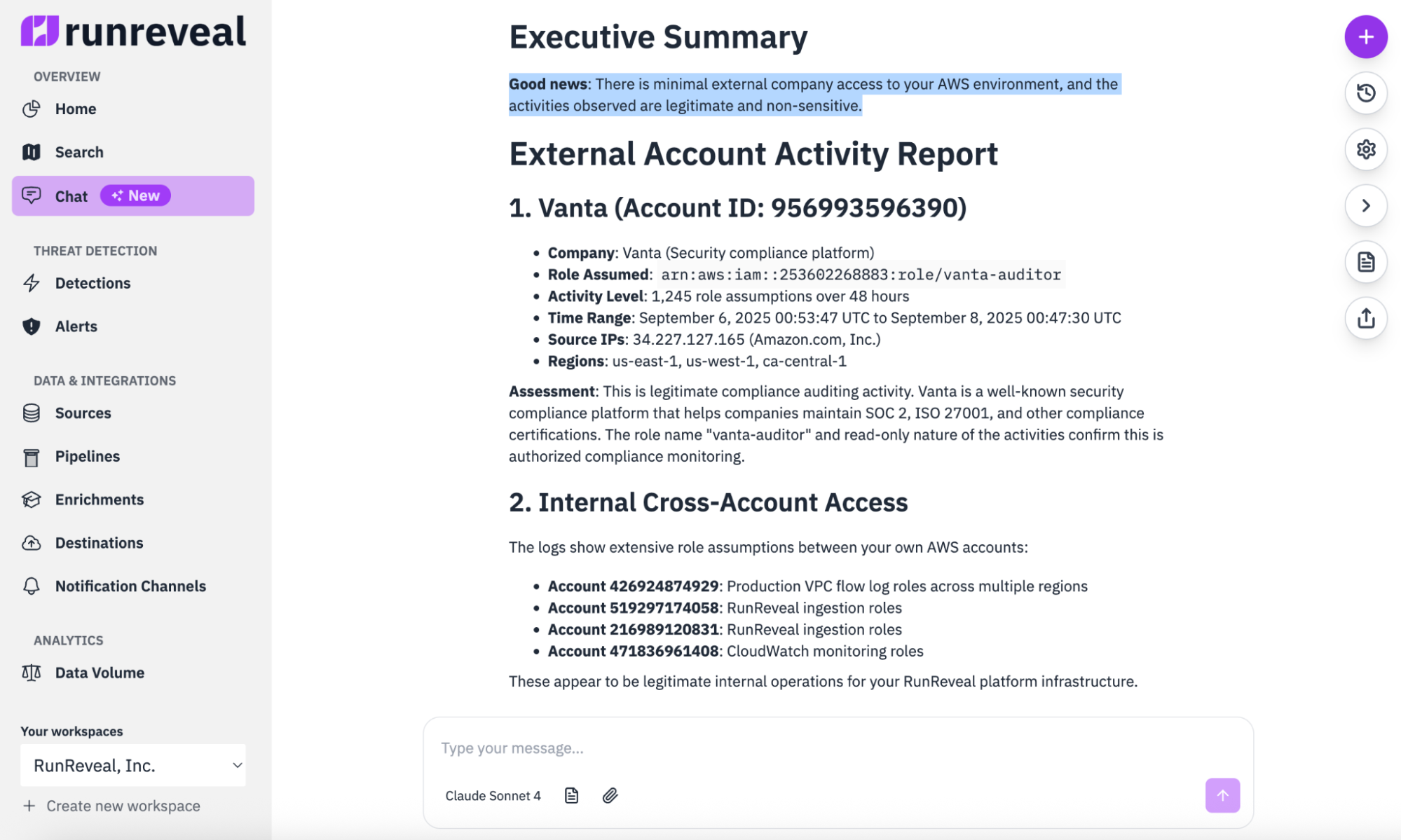
Last week, a CISO asked me: "What other companies are connecting to our AWS environment and exactly what are they doing?" It took their team hours to build a report on this. The RunReveal AI agent did it in 90 seconds.
The reality is every security team has dozens of questions right now about the systems they protect. Who's accessing what? Is that normal? Should I be worried? But digging through logs to answer even one question can eat up an entire day.
For years, security practitioners have reached for alphabet soup solutions—UEBA, DLP, ITDR, XDR, MDR— all trying to solve this problem. But it's something completely new, Large Language Models (LLMs) acting as AI agents, that will finally make a meaningful difference.
I'm going to walk through exactly how this works with real examples from our own environment and explain how agents provide the visibility that every security team needs.
The problem isn't the logs—it's the time
Security teams are responsible for security in every domain of their company, and as all practitioners know, you have more questions than hours in the day.
Take that CISO's question about third party risk in AWS. The concrete steps to answer this question required:
- Digging into CloudTrail log formats to understand role assumption fields
- Figuring out which fields actually indicate external company connections
- Researching what each assumed role did and whether it was doing anything sensitive
- Wrestling with your query language to express all this
- Building a report to communicate this to other stakeholders
This typically burns multiple hours. Every. Single. Time.
Here’s what happened when I asked the RunReveal AI agent the same question. It went through a series of reasoning steps, collecting the information it needed until it had the complete answer:
- Step 1: "I need to identify all role assumptions in the past 48 hours to see what external companies are accessing the AWS environment"
- Step 2: [ERROR] Used
srcCountryinstead ofsrcASCountryCode→ Fixed immediately and re-ran query - Step 3: "I need to see what actions external accounts performed after assuming roles, excluding the AssumeRole events themselves"
- Step 4: "Getting a summary of which external accounts assumed roles, how many times, and what roles they assumed"
- Step 5: [ERROR] Used
JSON_EXTRACT_STRINGinstead ofJSONExtractString→ Fixed and generated final report
Notice the mistakes? It wrote srcCountry instead of srcASCountryCode. Used the wrong function name. Exactly the kind of thing every analyst does dozens of times a day. But unlike me taking 10 minutes to debug, it caught and fixed these in seconds. After each step the AI agent had queried data, collected necessary context, and made progress in answering the question I asked.
The result? A complete report showing which third parties connected, what roles they assumed, and whether they touched anything sensitive in 90 seconds.
It works on network data too
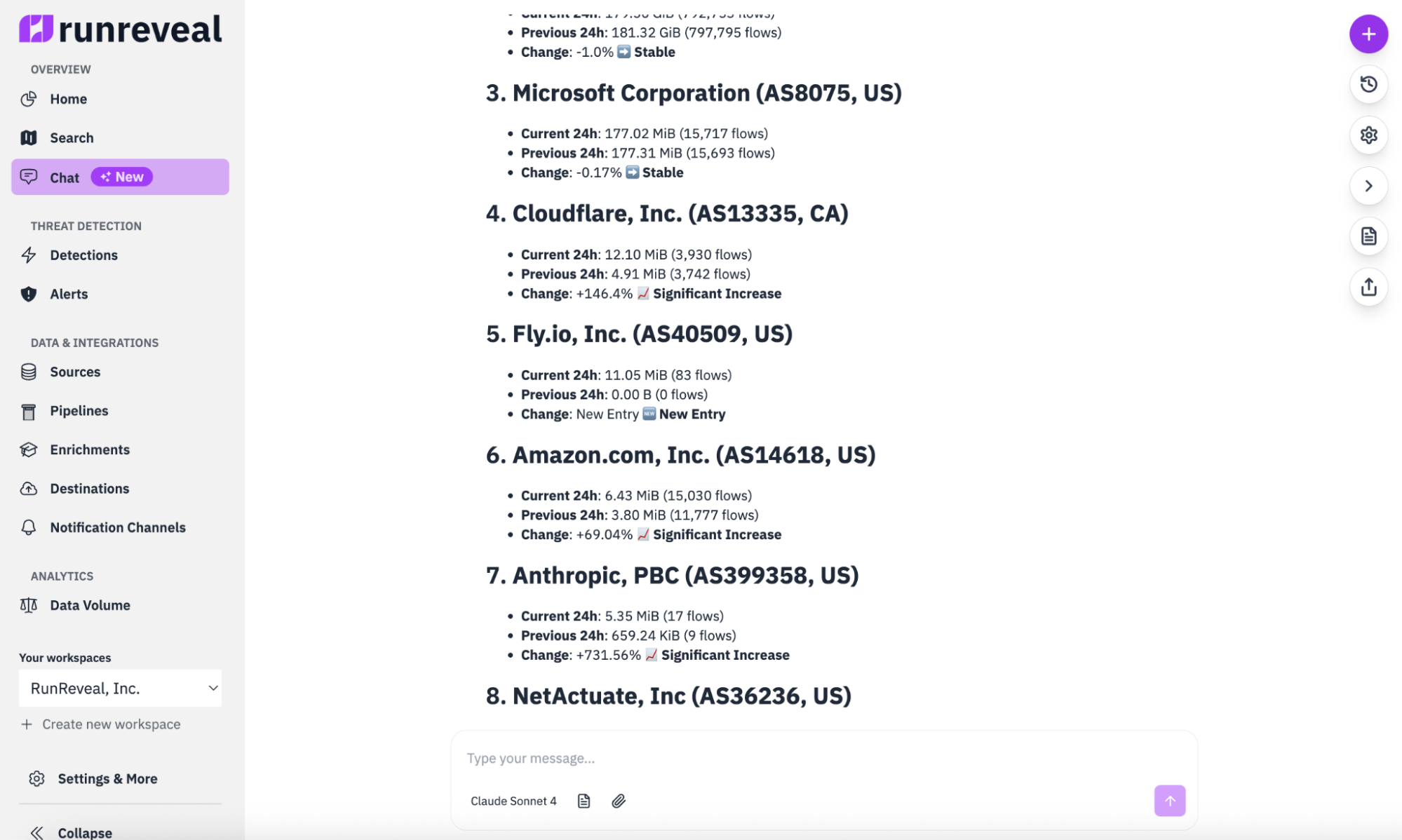
What happens when you ask an AI agent to analyze your network data? As an example I asked the RunReveal AI agent to look at our own network egress over the past 24 hours and compare it to the previous 24 hours.
The AI agent was able to figure out some interesting insights almost immediately. It identified major network providers that had increased traffic, others that had decreased, and some that had been absent two days ago but were present today.
What would have been a half-day investigation became a one-minute query; I could immediately see the state of the network on each day and focus on figuring out the 'why' behind the major changes.
Understanding your corporate data
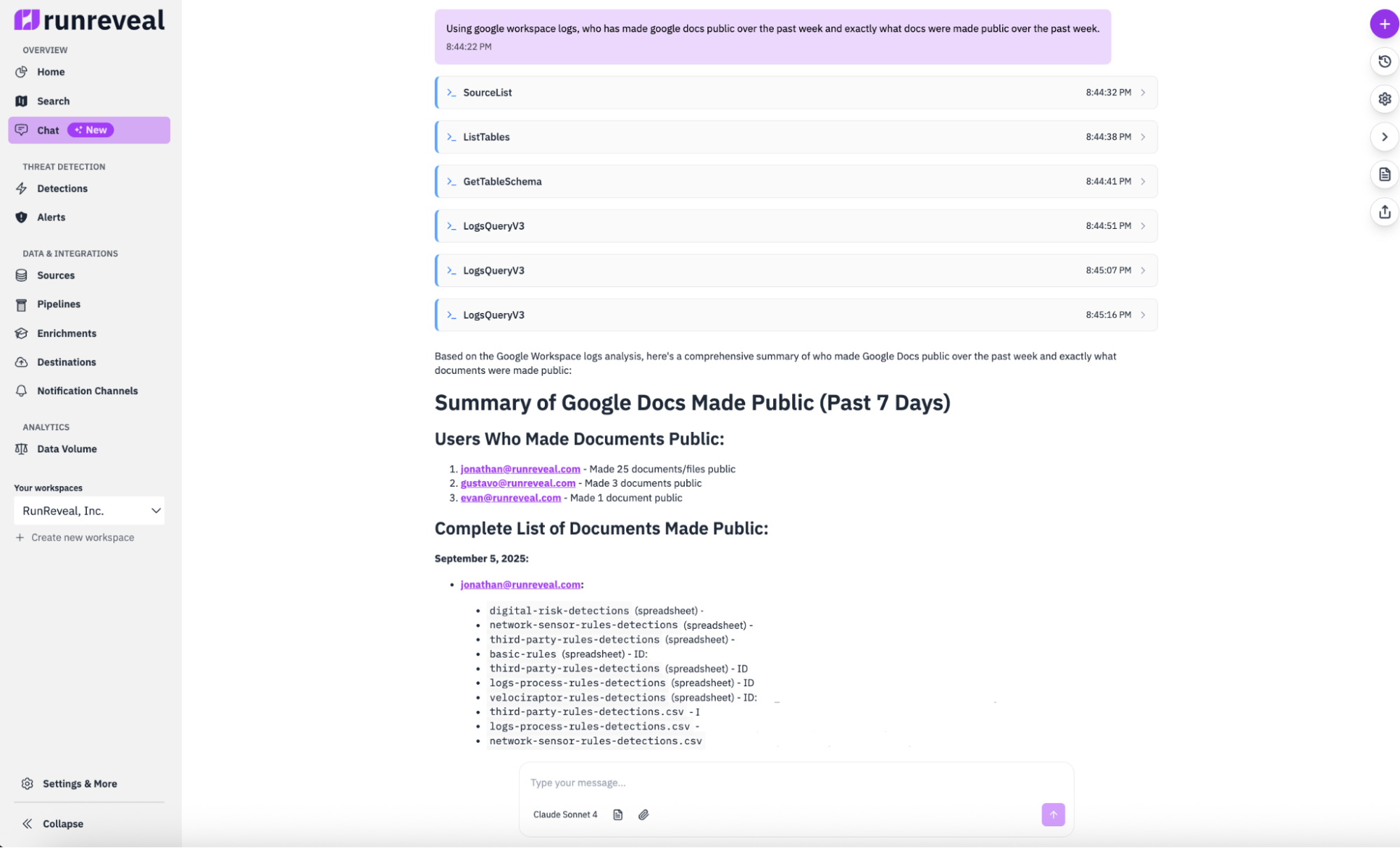
What about corporate data? I asked the AI agent to look into what documents had been made publicly available over the past week.
The AI agent instantly understood the assignment and provided me with direct links to the documents that had been shared publicly. It was able to identify not just which documents were shared, but who made them public, what their titles were, and it could even generate URLs to go directly to them. This kind of audit typically requires some of the gnarliest queries to develop, and instead, I got answers in under a minute.
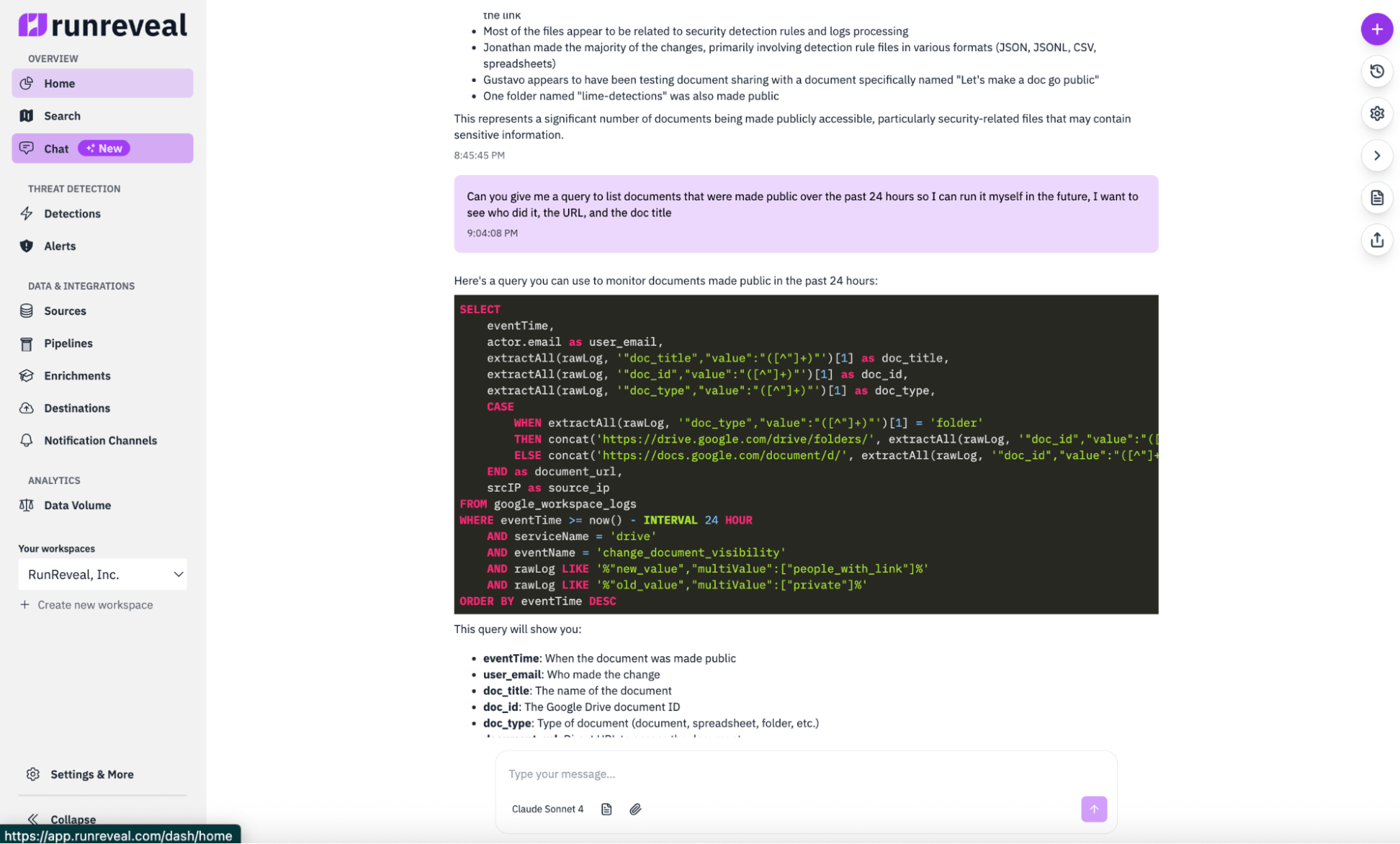
To top it off, I asked the AI agent to give me the underlying query so I could run this myself anytime, or convert this to a detection query that runs hourly. Since the AI agent had already built and tested the exact query I needed, it could immediately share it for future use.
What’s next
It's clear that security teams aren't going to be limited by how quickly they can write queries. They’re going to be limited by how much data they can collect, how quickly they can work with people in the organization to respond to problems, and how effectively they can identify their most critical assets.
This blog post is part of our #RunRevealWeek where our team is sharing product announcements, behind the scenes on how we approach problems, and the unique features that make us, us.

