RunReveal Supports Cloudtrail Logs
Store, alert, and query your cloudtrail logs.

Today we're excited to announce that RunReveal supports storing, writing custom alerts for, and querying AWS Cloudtrail logs. This is the first log source that we're supporting as part of our simple security data platform. With this initial release we're providing our customers with a power, simple, fast, and cost-effective security monitoring product.
RunReveal is built to give customers the capabilities they need to manage their security data. We've structured RunReveal to simplify the data ingestion process, give customers the ability to action their data within the log stream, and store their data.
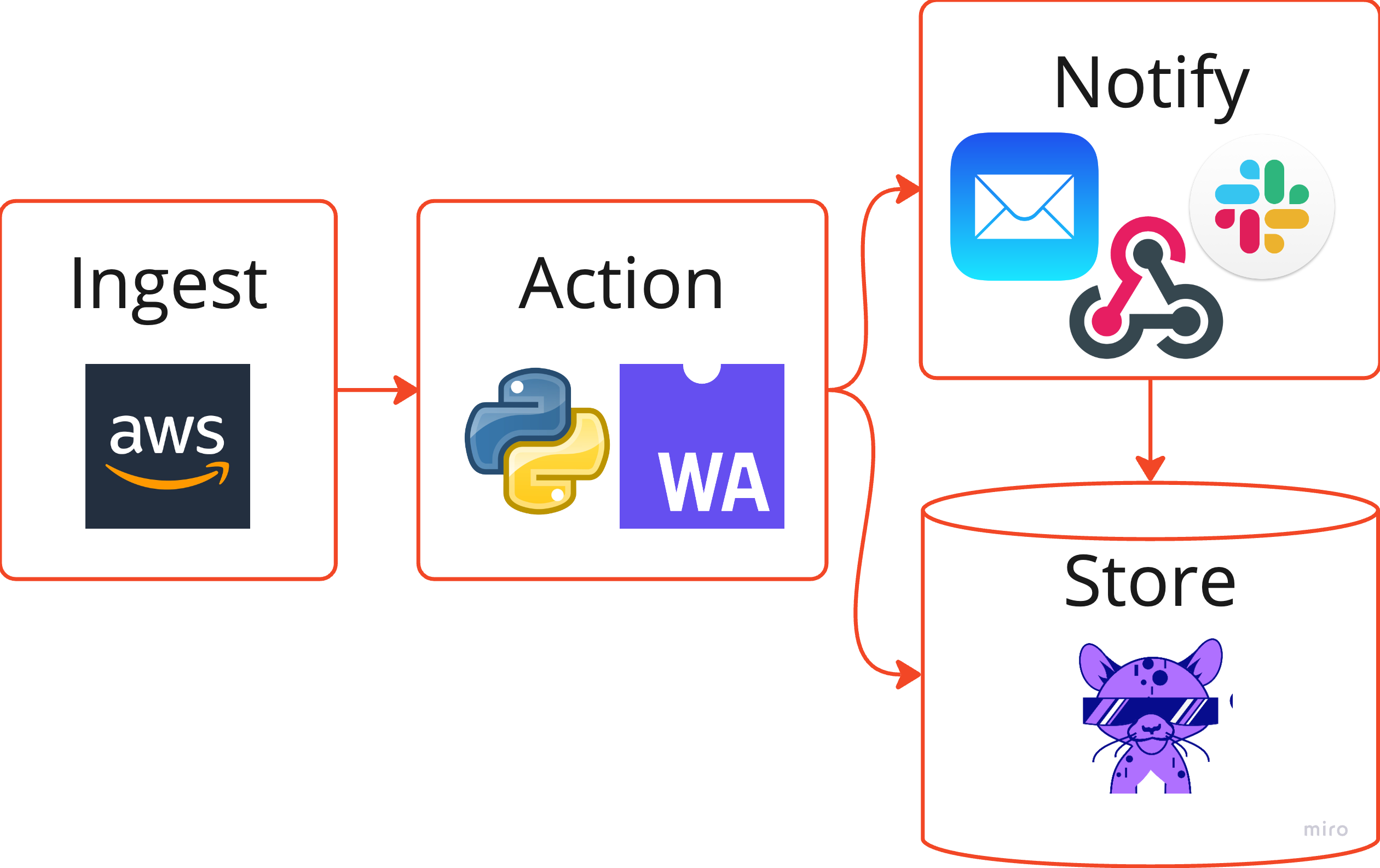
Setup
The main method for interacting with our product today is through the RunReveal CLI. We've set this up via a brew tap and installation and signup is a breeze.
$ brew tap runreveal/runreveal
$ brew install runreveal
$ runreveal init
Enter your workspace name: CoolWorkspaceTo begin collecting Cloudtrail logs you need to first tell us what AWS accounts are associated with your RunReveal account.
$ runreveal sources cloudtrail add "123456789, 234567891, 345678912"Next, you need to configure Cloudtrail to provide us with your logs. You can do that in a variety of ways but the simplest is to write your logs directly to the runreveal s3 bucket when creating your trail.

Writing an alert
The magic of RunReveal is in the flexible and performant programming interface. As an example, if you wanted to be aware whenever a state changing action is made in AWS, you can write a trigger that returns true whenever the readOnly field that is part of CloudTrail logs is set to False .
from runreveal import deep_get
def trigger(event):
return deep_get(event, "log", "readOnly") == FalseOnce you have a file with these contents, you can upload your trigger file to our API using the trigger subcommand.
$ runreveal trigger create --file new_key.py --name 'State Change Events'For each trigger you write, we pass all logs entries individually to each function you upload. Your functions are isolated in a WebAssembly runtime. Because of WebAssembly's flexibility, we'll likely support other programming languages, and provide helper functions and libraries in the future.
Once an event occurs, we will send your notifications wherever you've configured your alert notifications to be sent. Here's what a CreateAccessKey alert looks like when delivered to slack.
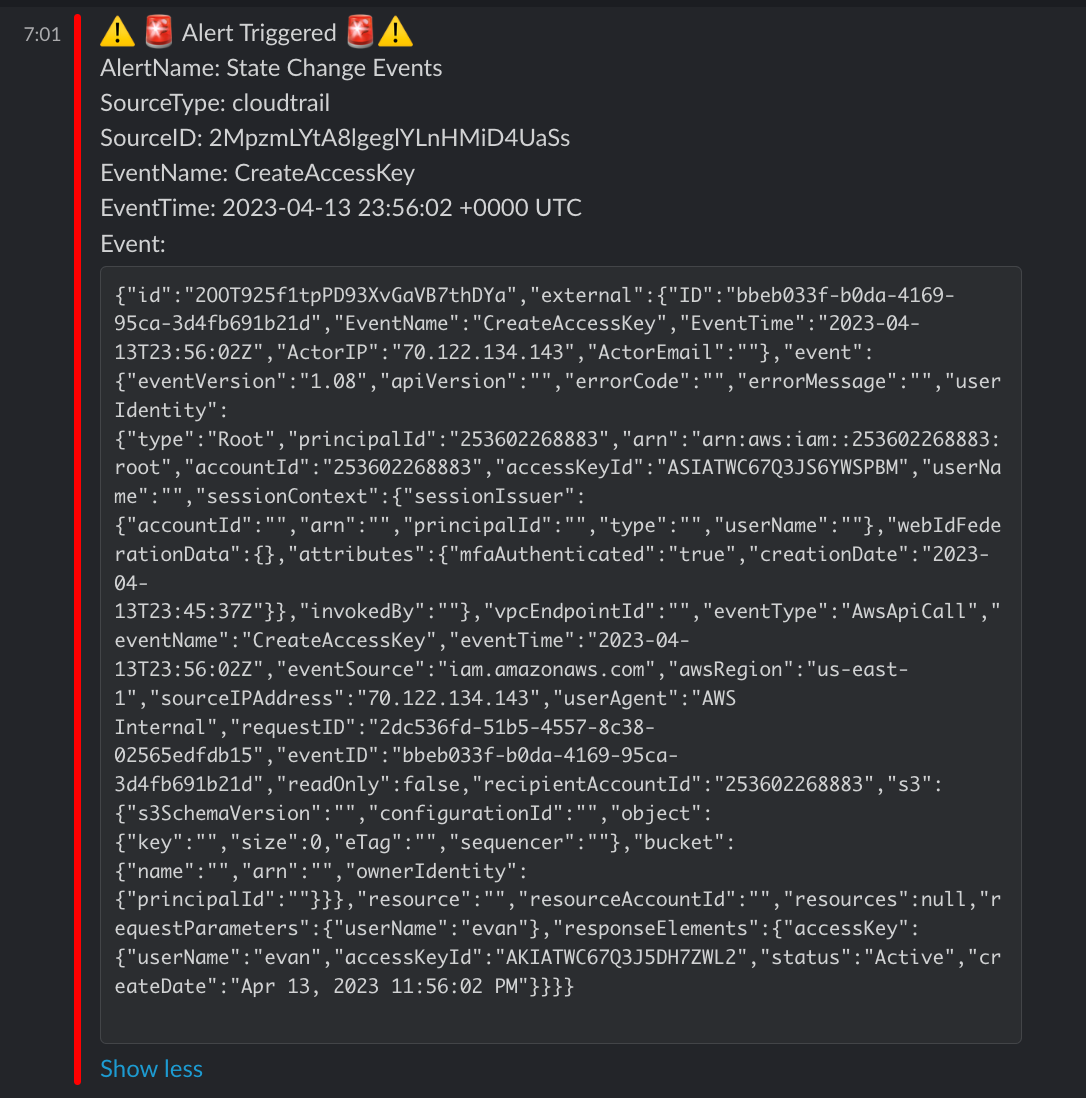
Searching your logs and triggered events
All of your Cloudtrail data is searchable. The logs we receive and results from your trigger functions are indexed and available in a lightning fast database. The search subcommand provides the ability to quickly filter logs with include and exclude for ad-hoc investigations.
:) runreveal search cloudtrail --include readonly=false --include username=evan --num 5
5 rows returned
Time Identity Source IP Event Name
2023-04-12 02:07:44 +0000 UTC arn:aws:iam::253602268883:user/evan 12.23.34.45 GetCallerIdentity
2023-03-31 21:37:23 +0000 UTC arn:aws:iam::253602268883:user/evan 12.23.34.45 GetSecretValue
2023-03-31 21:32:31 +0000 UTC arn:aws:iam::253602268883:user/evan 12.23.34.45 GetSecretValue
2023-03-31 21:32:31 +0000 UTC arn:aws:iam::253602268883:user/evan 12.23.34.45 GetSecretValue
2023-03-31 21:32:30 +0000 UTC arn:aws:iam::253602268883:user/evan 12.23.34.45 GetSecretValue
The RunReveal search capabilities are fast enough to get instant answers, and without needing to worry about runaway costs from reading too much data at once. This query returns in no time at all.
:) time runreveal search cloudtrail --include readonly=false --num 100 --include username=evan 1>/dev/null
100 rows returned
runreveal search cloudtrail --include readonly=false --num 100 --include > 0.03s user 0.02s system 4% cpu 1.313 total
:)
Continuing our mission
This is just our first logging source but our core pipeline is taking shape. Our aim in the near term is to add support for all kinds of logs that our customers need, and notification tools that customers need in order to understand their environments.
RunReveal's next big goal is to make the data you store with us accessible and usable for all types of other use cases. We believe that the data you store in RunReveal is your data, and should be usable for all kinds of purposes your security team may have. We hope to share developments in this space soon.
If you're interested in our product get in touch with us at contact@runreveal.com

