Introducing Automatic Enrichments. Rewriting logs with the latest threat feed data.
Today we're excited to announce automatic enrichments and we're making them available to all RunReveal customers. Automatic enrichments are your security team's easy button for contextualizing your logs with managed enrichment rulesets. Today we're launching an IP threat intel enrichment and an automatic domain based threat intelligence enrichment.
Our managed enrichments provide our customers with the ability to enrich their logs with the latest threat information with a single button press, and today we're enriching over 250,000 logs second at peak processing times.
You'll remember just a few weeks ago we announced custom enrichments so our customers could build their own enrichments. After announcing that we immediately got to work building automatic enrichments on top of the same enrichments API we give to our customers and pushing that product to the extreme.
Managed enrichments are your easy button for simple and effective detections
Managed enrichments relies on the fact that all RunReveal logs are normalized into a consistent schema. Enrichments work by looking up specific fields in your logs and based on the value of those fields additional useful information is written to the log.
Our first automatic enrichment reads each log's source IP across, compares it to a list of about 125,000 IP addresses that is updated every 15 minutes, and adds additional information about any relevant threats feeds the log's IP was found in.
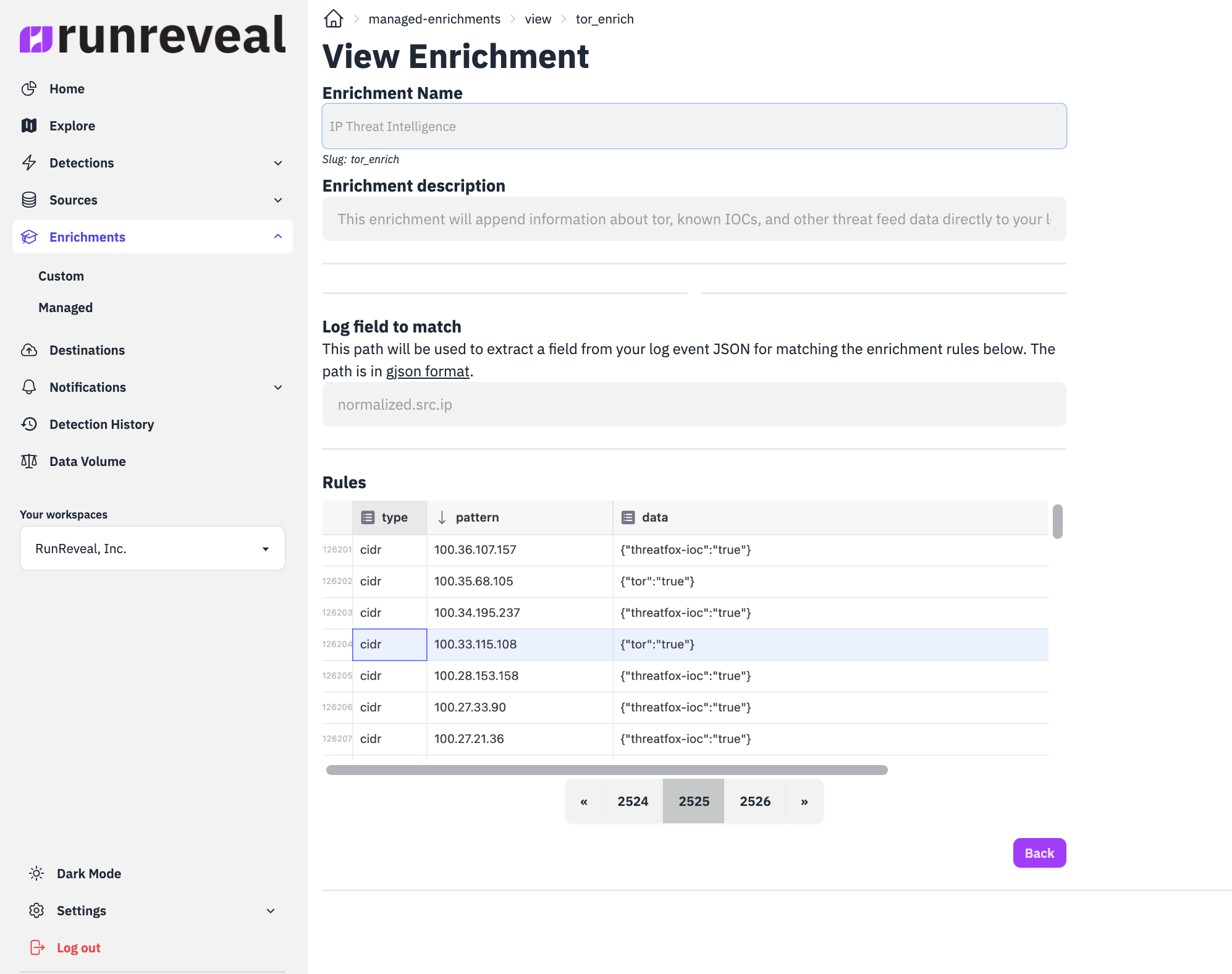
Our customers don't need to worry about complicated joins inside their SIEM, the format of the log, data-decay issues like previously bad IPs now being reported as good, and instead can just flip a switch in RunReveal to begin enriching every log source they have.
The best part is that this feature was built for massive scale so it's available for every usage tier, including our free tier.
What it looks like to use automatic enrichments
It's actually just a toggle to get started with managed enrichments. We wanted to make the experience simple, and before you enable a managed enrichment we show you exactly what log types it will work for.
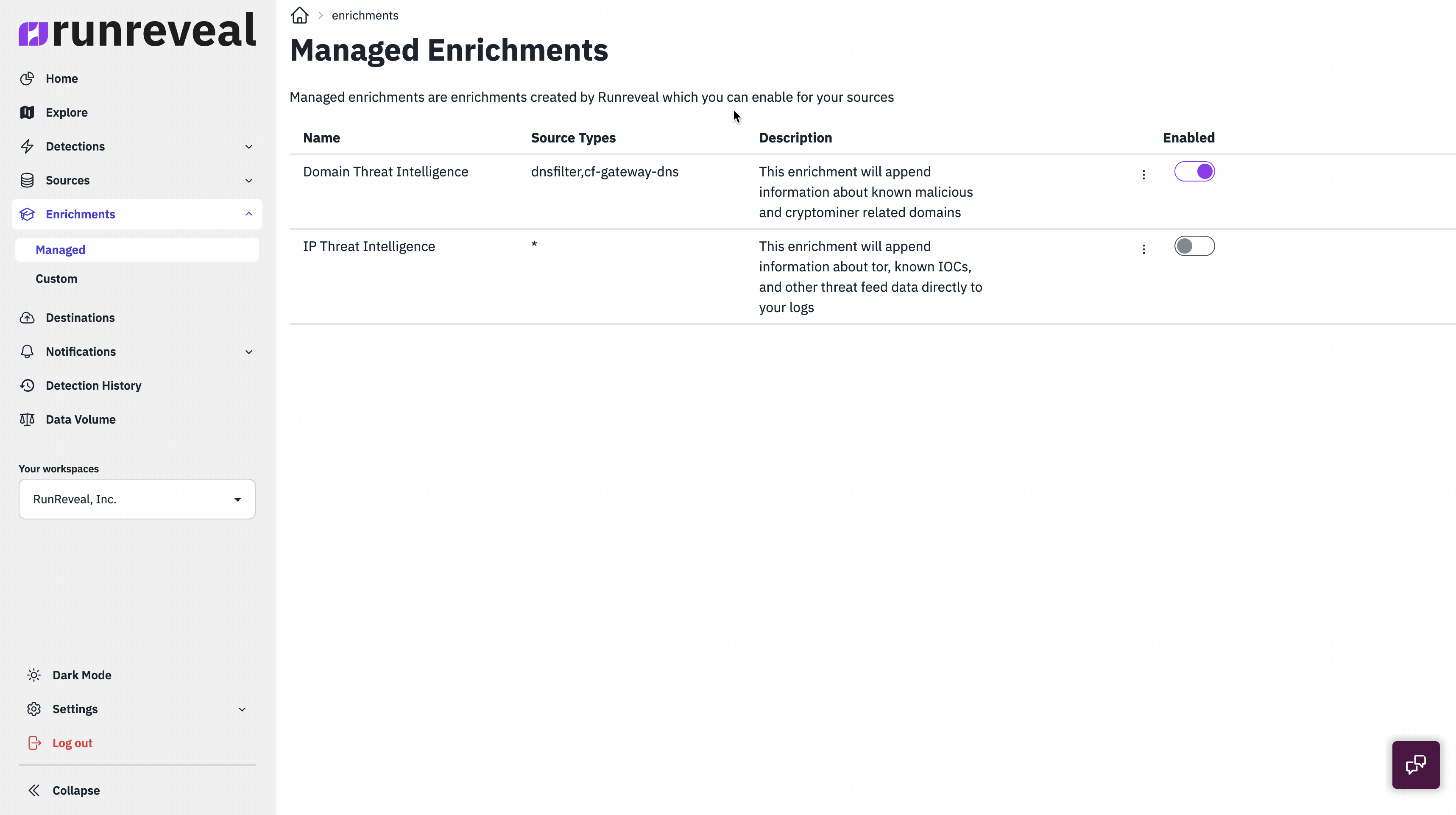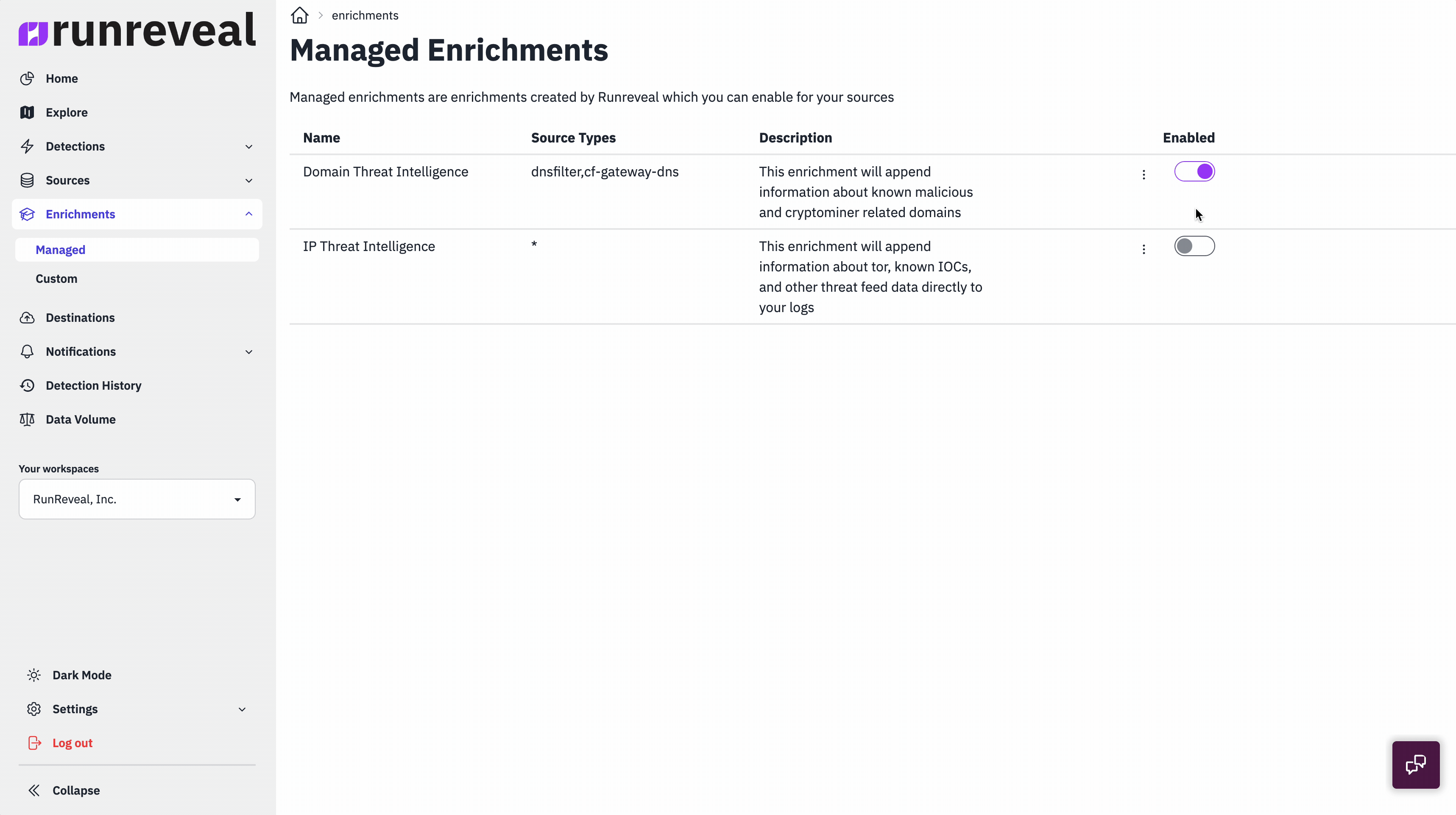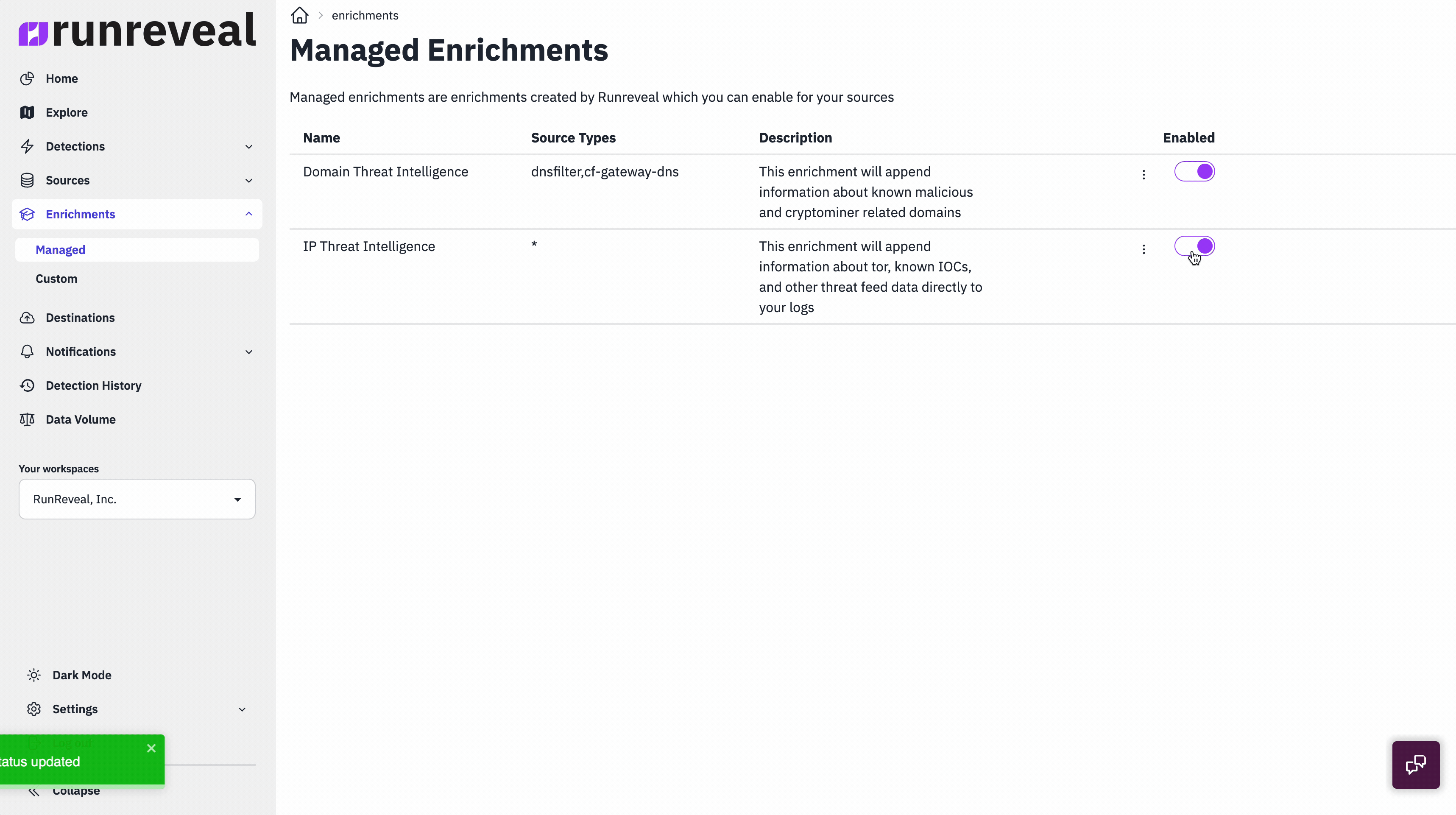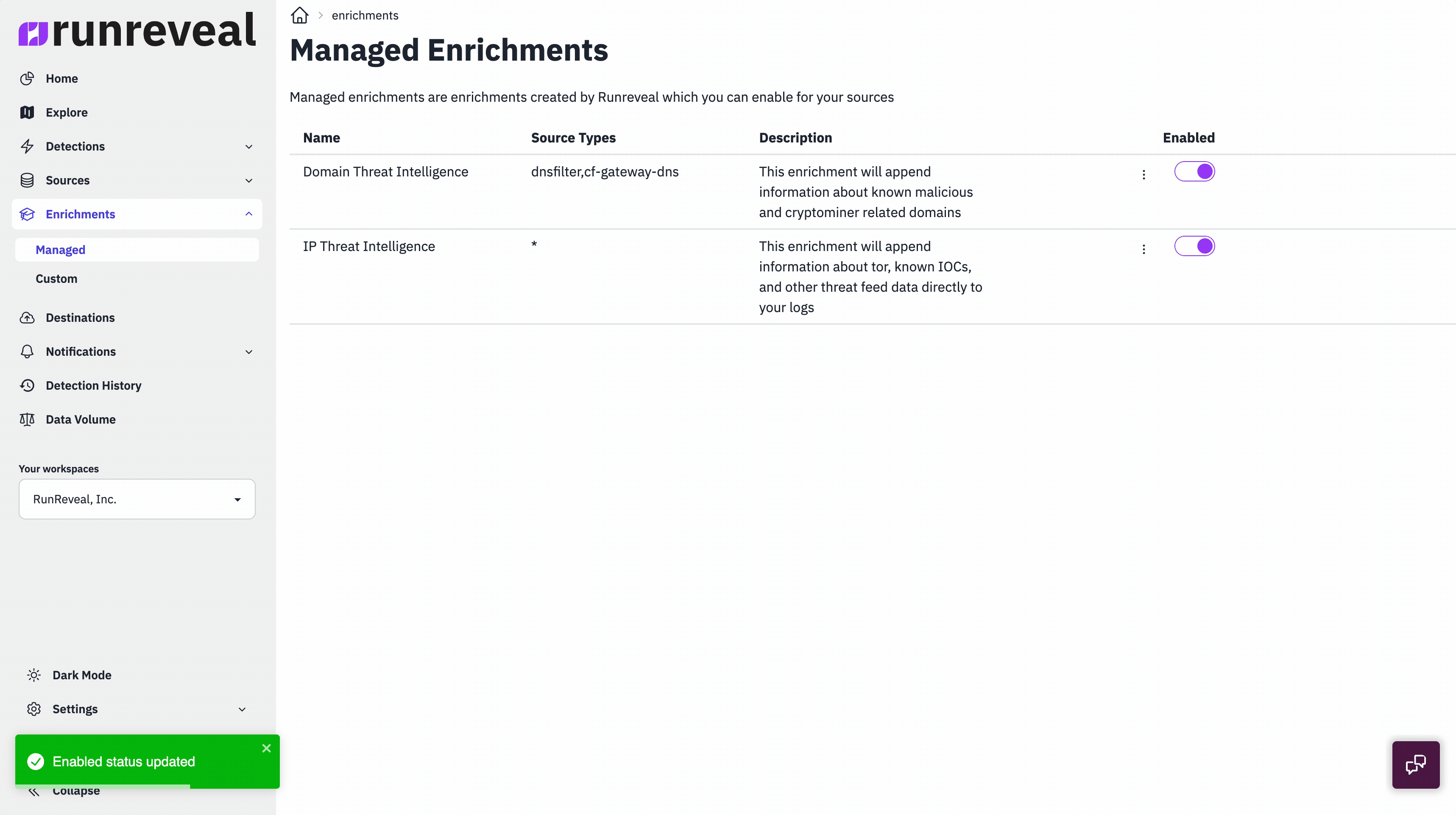
Immediately RunReveal will start comparing your logs to information about the IP threat intelligence we've collected and keep the threat intel refreshed in the background. You'll notice that the enrichment column across every log type will contain any additional enrichment data in the OCSF enrichment schema.
We turned on logging from our nginx server to test out the enrichment of these logs in RunReveal. The result was that we were able to instantly filter out the signal from the noise and locate the bad actors scanning our website. In this case we were being scanned from a shady VPN provider's IP range!
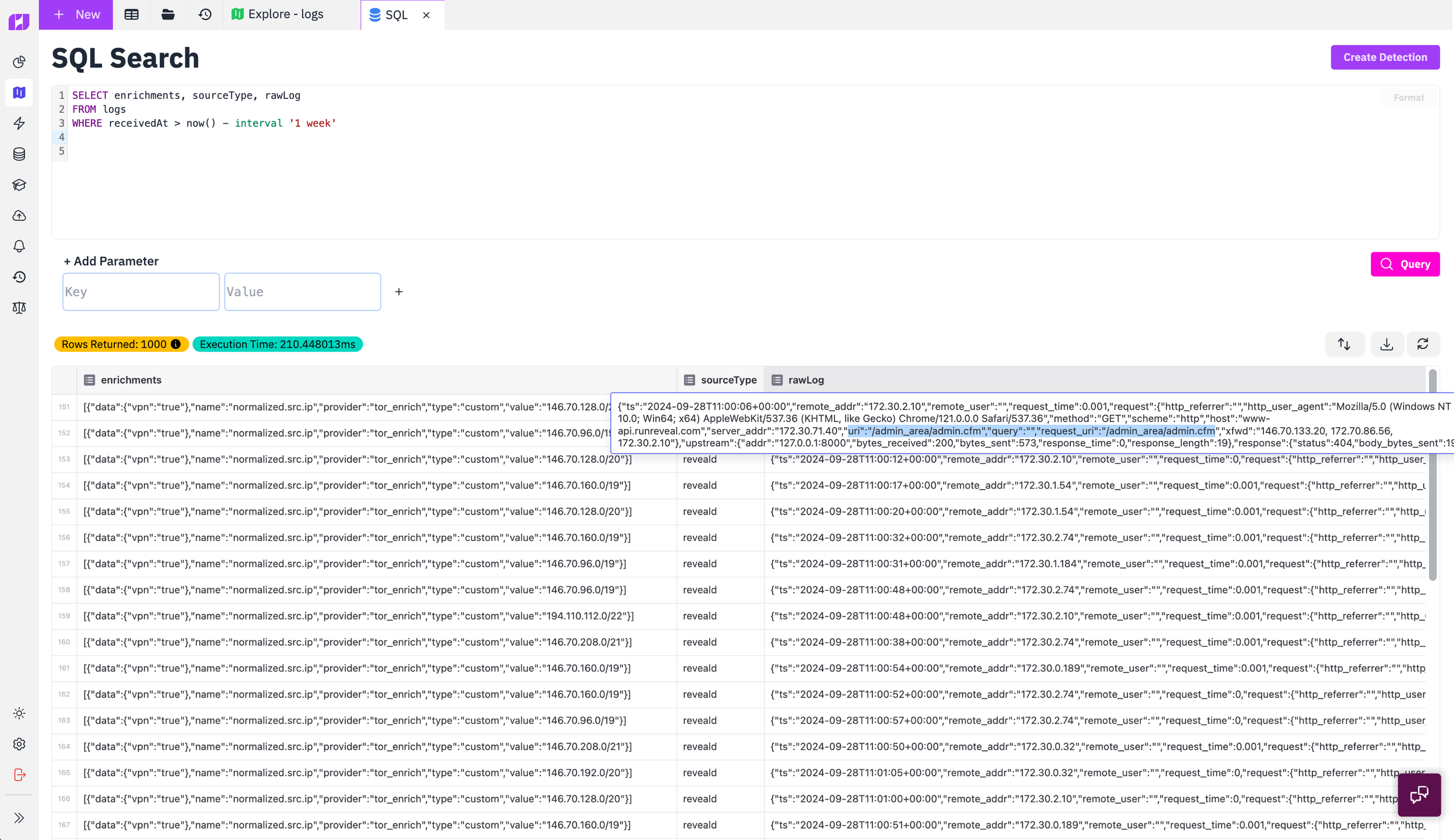
Malicious scanning is to be expected and nothing to worry about but we can use the enrichment data for alerting too. In addition to saving your logs at your configured destinations we've configured our sigma detection engine to support alerting immediately and saving the log to our signals table for more correlation. Here's what a sigma detection would look like if we wanted to alert on all Tor traffic that hits the nginx in front of our API.
title: Nginx Scanning Tor
description: Detects http requests to our website from tor
logsource:
service: reveald
detection:
selection:
tor: true
condition: selection
level: high
The enrichment context is flattened into the sigma evaluation engine and we can quickly and easily build detections just by looking up the data that was appended to the log.
Having the ability to enrich without the reliance on a SIEM is incredibly important if you want to avoid data-decay issues. Our enrichment engine is super fast and efficient which means we can power the detection engine for huge workloads at a lower cost than has previously been possible, and it's compatible with our destinations, detections, and all other RunReveal features we've built. Best of all we turned this into a single button without any additional configuration necessary.
What's next
Well, we didn't actually tell you how this works under the hood and there was a lot of the amazing engineering that went into it. We've already written a blog sharing all the technical details about how this works, how we integrated it with our streaming sigma detections, and how we're able to search over 126,000 CIDR ranges over 250,000 times per second.
Coming soon we'll have more blogs showing interesting use cases for RunReveal, product innovation we haven't yet talked about, and more technical deep dives into the ways our products work.
If you want to learn more about managed enrichments, RunReveal, or how we can help your detection program then contact us or click here to get a demo

