Detecting Okta's Oct 20, 2023 Indicators of Compromise with RunReveal
Okta announced a security incident today related to their technical support systems. The announcement gives an overview of the issue, but doesn't contain a complete timeline or technical details of the attack.
Krebs on Security and BeyondTrust both wrote more information on the breach, with BeyondTrust claiming to have discovered evidence of the breach as far back as Oct 2nd. BeyondTrust's blog says their suspicions that Okta was breached were confirmed yesterday by Okta's security leadership team in a private zoom call. Security breaches take time to investigate, so it's likely Okta will share more information as their investigation concludes.
As part of the announcement, Okta shared IPs and UserAgents used by the attackers who compromised their support systems. Many of the IP addresses are associated with a commercial VPN service (Browsec), while the final three being associated with a few different commercial VPS providers. Okta customers should investigate if their logs contain any of these indicators of compromise.
We've added an alert to RunReveal's pre-made detections, and enabled the detection by default, so our customers can be aware if any of these IoCs show up in their logs. Additionally, we proactively reached out to all RunReveal customers who's logs contained any of the published IoCs.
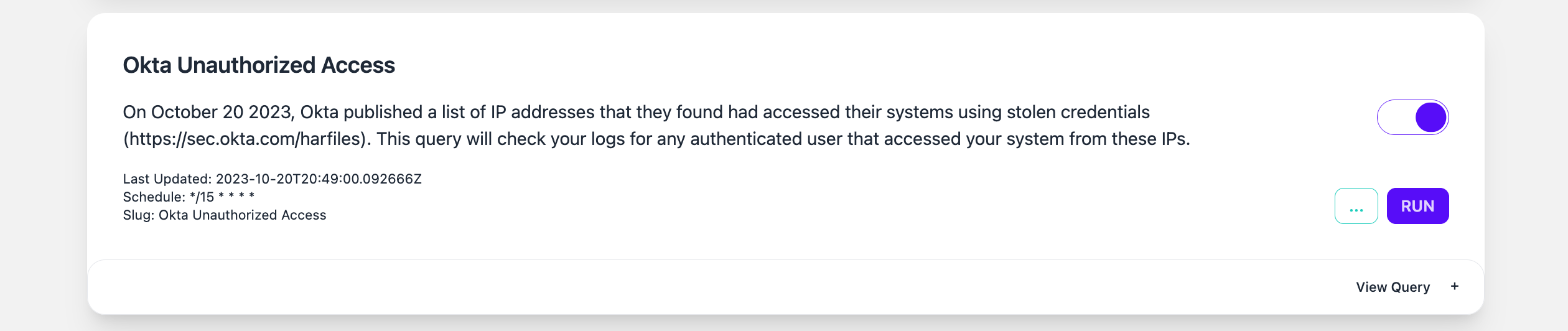
What should I do if I see the IoCs in my logs?
If you see any of the IoCs you should investigate further. The questions you'll likely want to ask yourself are:
- What is my company's incident management process?
- Is this an audit log of an authenticated user at my company, or something that showed up in my logs from the outside (like an HTTP log)?
- If the log was generated by an authenticated user, are they also a user of the commercial VPN provider that the threat actors used?
Make sure you document the findings of your investigation to share with other decision-makers at your company. If you'd like to search for all of your RunReveal logs that contain these indicators of compromise, you can do-so with these two queries.
This query will search your logs for the malicious IPs:
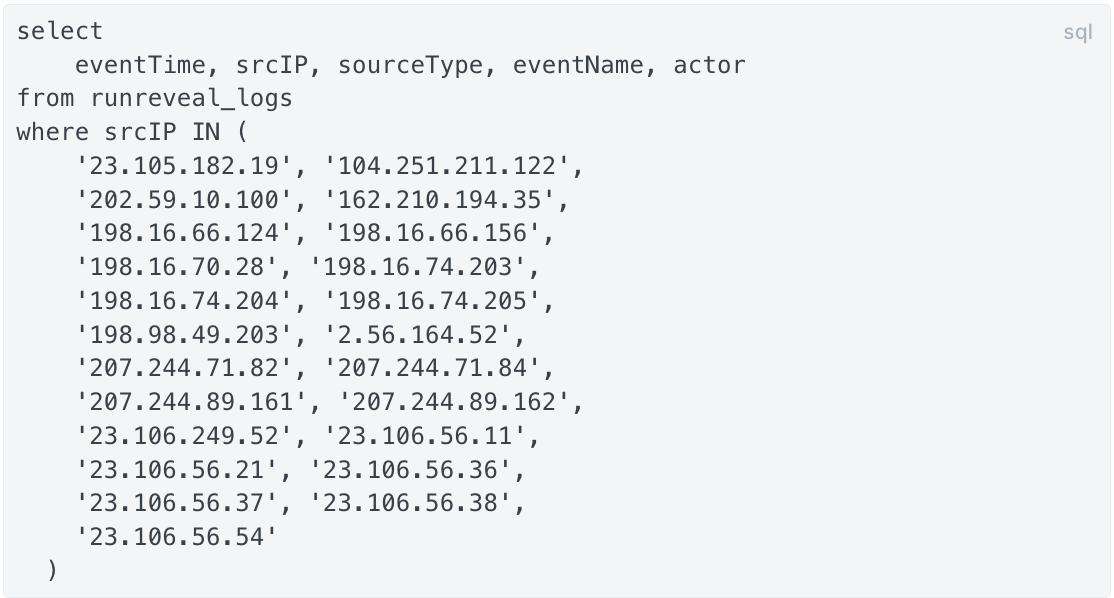
select
eventTime, srcIP, sourceType, eventName, actor
from runreveal_logs
where srcIP IN (
'23.105.182.19', '104.251.211.122',
'202.59.10.100', '162.210.194.35',
'198.16.66.124', '198.16.66.156',
'198.16.70.28', '198.16.74.203',
'198.16.74.204', '198.16.74.205',
'198.98.49.203', '2.56.164.52',
'207.244.71.82', '207.244.71.84',
'207.244.89.161', '207.244.89.162',
'23.106.249.52', '23.106.56.11',
'23.106.56.21', '23.106.56.36',
'23.106.56.37', '23.106.56.38',
'23.106.56.54'
)This query will search for the user agents used by the attackers:
select
*
from
http_logs
where
httpRequestUserAgent in (
'Mozilla/5.0 (Windows NT 10.0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.7113.93 Safari/537.36',
'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.83 Safari/537.36'
)Keep in mind...
It's likely more information will come out about the incident given the news broke only a few hours ago. It's important you revisit the incident as more information becomes available because it could impact the conclusion you reached during your investigation.
RunReveal will update the detection we provide, and notify any impacted customers if new indicators of compromise are released.

